DNS Firewall to Enhance Your Networks Security | CleanBrowsing
DNS is the internets lookup table, it builds a bridge between the domain name (e.g., perezbox.com) and the IP address (e.g., 184.24.56.17). The IP address being where you can find the server that hosts the domain. In addition to its job as a lookup table, it can also serve as an effective security control.
DNS is light weight, doesn’t require an installation, highly effective, conforms to the TTP’s employed by attackers, and, more importantly, affordable.
This article will introduce the concept of a DNS Firewall (Protective DNS) and encourage you to think of it as an additional layer in your security governance program.
Mitigating Attack Tactics
Understanding how attackers leverage domains in their attacks allows us to appreciate how effective DNS can be. Here are few tactics, techniques and procedures (TTP) leveraged by attackers that helps illustrate the point:
| Benign Websites | An attacker compromises a benign site (domain), it’s used to distribute malware, or perform other nefarious activity (e.g., Phishing, SEO Spam, etc…) |
| Malicious Site | An attacker creates a malicious site (domain), it’s sole purpose is to distribute malware, or perform other nefarious activity (e.g., Phishing, SEO Spam, Dropper, etc…) |
| Command & Control (C&C) | Command and Controls (C&C) is what an attacker uses to facilitate their orchestration. Payloads will phone home to C&C’s for instructions on what to do next. |
The scenarios above both leverage Fully Qualified Domain Names (FQDN) for the site to render.
Example 1: The 2019 Mailgun Hack
In 2019 there were number of WordPress hacks that exploited a vulnerability in a well known plugin. This exploit affected thousands of sites, including the popular Mailgun service.
Attackers used their access to embed JS code on the sites that would initiate calls to a number of different domains: hellofromhony[.]org, jqueryextd[.]at, adwordstraffic[.]link. These domains would then initiate different actions (including stealing credit card information) depending on the request.
The embedded JS payload initiates a DNS request.
Example 2: Managing Multiple Servers
Assume you are an organization responsible for 100’s, if not 1,000’s, of servers. An attacker bypasses your defenses and moves laterally through the network. In the process, the attacker sprinkles droppers across the network designed to phone home to their C&C.
The phone home initiates a DNS request.
Example 3: – Mitigating User Behavior (Phishing)
If there is something we can always count on is curiosity always kills the cat. Users always click.
Clicking the link initiates a DNS request.
The Effectiveness of DNS
The examples above are only a few that quickly illustrate how DNS can be leveraged to mitigate attacks. To help support the case, we can look at the Verizon Data Breach Investigations Report (DBIR).
Analyzing a five year period, 2012 through 2017, you find that close to a third of the 11,079 confirmed data breaches were identified to be threat actions that DNS could have mitigated (source: Global Cyber Alliance 2018). Having a security control with 1/3 control relevance is pretty impactful for any organization.
With DNS as the backbone of how the internet works, any time a domain is queried DNS is, by design, triggered. Consider the different scenarios above, and you quickly realize that DNS is the gateway that all requests have to pass through.
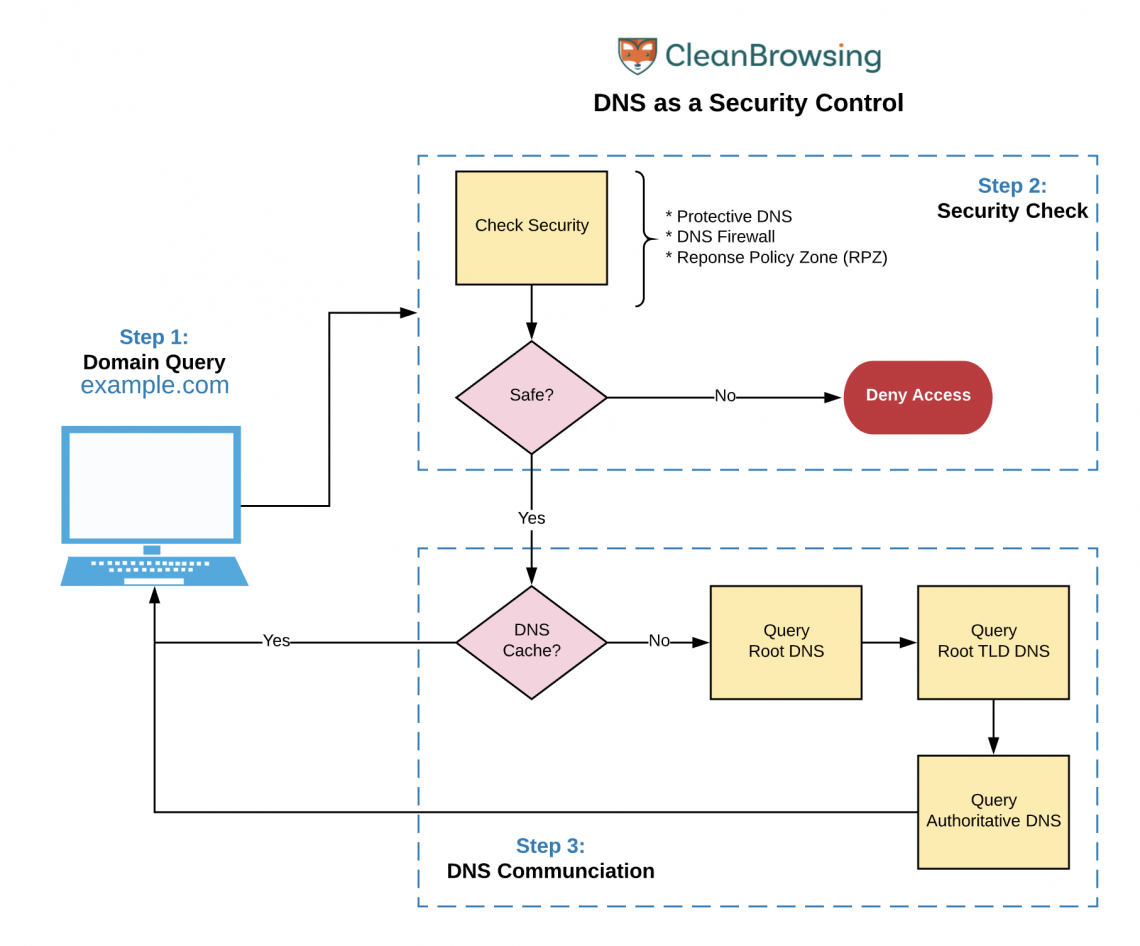
The illustration above shows how and where a DNS Firewall might fit in your networks architecture.
The DNS firewall will inspect the initial query, verifying that it’s safe, before allowing it to proceed with the rest of the DNS communication chain. There are a number of great DNS Firewall services; I personally leverage the CleanBrowsing Security Filter (it’s Free and highly effective).
IPv4 address: 185.228.168.9 and 185.228.169.9
IPv6 address: 2a0d:2a00:1::2 and 2a0d:2a00:2::2
If you run your own internal DNS you want to look into leveraging Response Policy Zones (RPZ). RPZ is a security specification and protocol to enhance DNS resolvers with security intelligence about the domains it is handling. It allows a local DNS resolver to restrict access to content that is malicious or unwanted. It allows you to create your own DNS Firewall.
This deployment is applicable to large organizations and homes alike. :)
