My WordPress Security: Providing You a Safe Online Experience
Over the past few months I have started to come to terms with the fact that I’m a blogger.
Yes, I am the CEO of Sucuri, and I’m known for my engagements about security on a variety of fronts, but when you really boil things down: I have a a lot to say. It’s why I write about Brazilian Jiu Jitsu on Tony on Jiu Jitsu, and everything else on this very blog. I also spend a good amount of time reading, updating and editing every post we share on the Sucuri Blog.
While I can fight it, I realize however it is a losing battle and of all my accomplishments in life, blogger is likely what I will stay through the up’s and downs.
Because of that it occurred to me that I should probably share some some insights into how I ensure that you’re experience on my blog is a safe one.
I wrote and shared some of these points a year and a half ago on WPEngine’s blog (How Tony Perez of Sucuri Sets Up His Own Security), but thought it’s perhaps time I update this information. With the proliferation of WordPress Security, it only becomes more important we share practical applications and configurations so that others can also follow suit.
I think what you’ll notice by the way is how little I do within WordPress, the application I have chosen to do most of my blogging on – across all platforms. This will also be more applicable for those of you that are using custom installs of WordPress from the WordPress.org website.
Functional Isolation of my Environment
This isn’t discussed much, or written about, but it’s one of the more important things you can do as a website owner. For me it’s about closing as many of the points of entry as possible.
For instance, I operate all my websites in their own environments. My main properties – Perezbox, Tony on JiutJitsu and Tony on Security, all operate within their own Virtual Private Server (VPS). The server is not heavy duty, but it’s not the lowest model either.
I run a bare bone CentOS configuration with Linux, Apache, MySql and PHP. This is also known as a LAMP stack and what most of the shared hosts operate for you.
I do not run anything that doesn’t belong on the server:
- CPanel is not configured
- WHMCS is not configured
- Email Server is not configured
- Baggage from old installs are not configured
I also run continuos updates via a cron job to ensure the latest updates are patched. Remember the Bash vulnerability?
That’s it, I run a super clean environment. I wrote about the process of my
install back in June of 2012, and the steps still hold true today.
WhiteListing is Highly Effective
I also employ a highly effective whitelisting strategy across my entire stack, on all properties. The strategy is very simple and easy to follow:
- Whitelist everything
All kidding aside, I’m serious. From the server to the application, I whitelist all access. This means that you cannot access my server via SSH unless your IP has been added to the server firewall settings, which by the way I don’t use any fancy server level firewalls, I leverage good ole IPTABLES.
I also use a highly disconnected VPS where I funnel all my traffic. It lives off in the online ethers by itself where it’s only function is to handle my traffic, regardless of where in the world I am. The only service it runs is SSH and it only accepts pings from my predefined locations. I use a custom server script that allows me to update the IP anywhere I go. This server gives me one constant IP that i can whitelist across all other environments.
I don’t use public or private VPN services because honestly, I just don’t trust them. I do use GetCloak from time to time on my mobile devices when I’m forced to leverage public WiFi, but when the laptop comes out, it’s all about my personal VPN.
Quick Side Bar
I really don’t buy into the nonsense people and organizations tell themselves about using a whitelist strategy. It’s too hard, I can’t get people to leverage it, etc… All these explanations I categorize as rubbish and laziness, based on very little consideration for their security, regardless of how much they say they really care.
What they don’t realize is this approach is highly effective, and quite possibly one of the more effective strategies, with the best results, they can take. Especially for organizations with budgets.
My Application Security Configuration: The Tools
The two hardening steps I do take at the application level are:
- Disabling the Editor from WP-ADMIN for both Themes and Plugins
- Disable PHP Execution in various folders (Uploads, WP-Includes, and a few others)
I achieve these two via the hardening feature in the Sucuri Security Free WordPress Security Plugin. This video quickly walks you through how that hardening feature works:
That’s all that I do at the application level. The plugin is also used for my day to day maintenance activities, which I’ll share more on below.
From there I move all my focus to my security products. I use the following three services:
- Sucuri Website AntiVirus
- Sucuri Website Firewall
- Sucuri Website Backups
1. Sucuri Website AntiVirus
Granted, I’m very partial here but I eat my own dog food.
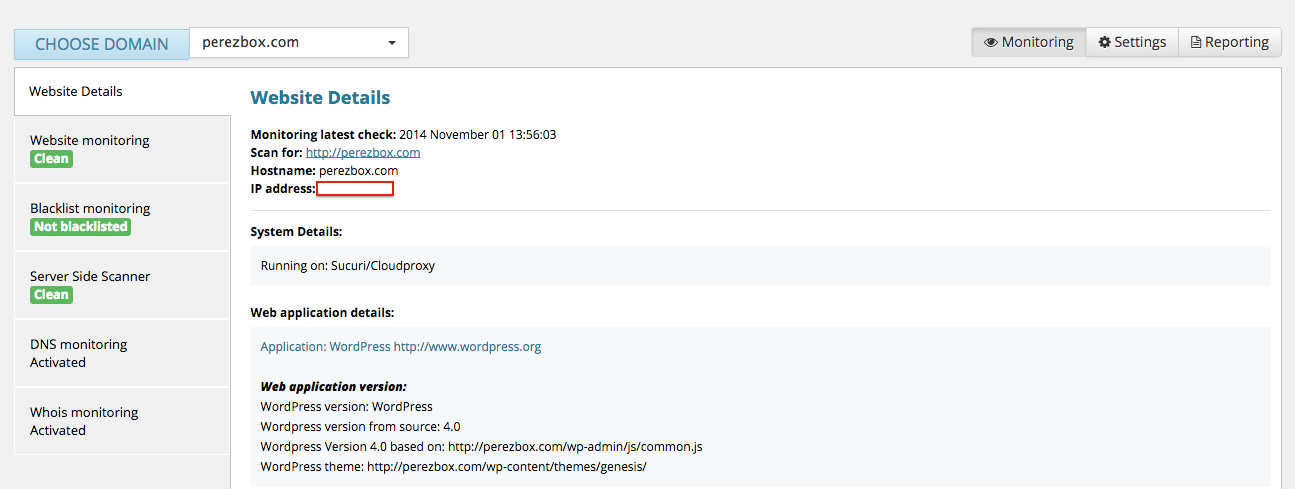
What I’ve realize though is that almost everyone underutilizes the services the Website AntiVirus offers. Here is my configuration:
What you should notice is that i have a few things configured that most don’t, not because it’s not available to them but because they just don’t configure it:
- Security Scanning (looking for malware and other security incidents – obvious)
- Blacklist Monitoring (Default)
- Server Side Scanner (Ideal for Backdoors, Phishing and other anomalies – yet most don’t configure it)
- DNS Monitoring (Almost no one configures)
- WHOIS Monitoring (Almost no one configures)
These four monitoring configurations give me a very good view of the state of things on a daily basis. What’s really awesome is that every week I get a nice a little report giving me a quick summary of things as well:
Once my monitoring is configured I make sure my notifications are set so that in the event something is triggered I get an immediate notice and can appropriately respond. Last thing I want is for my properties to be used maliciously and potentially affect my wife, friends or family members.
2. Sucuri Website Firewall
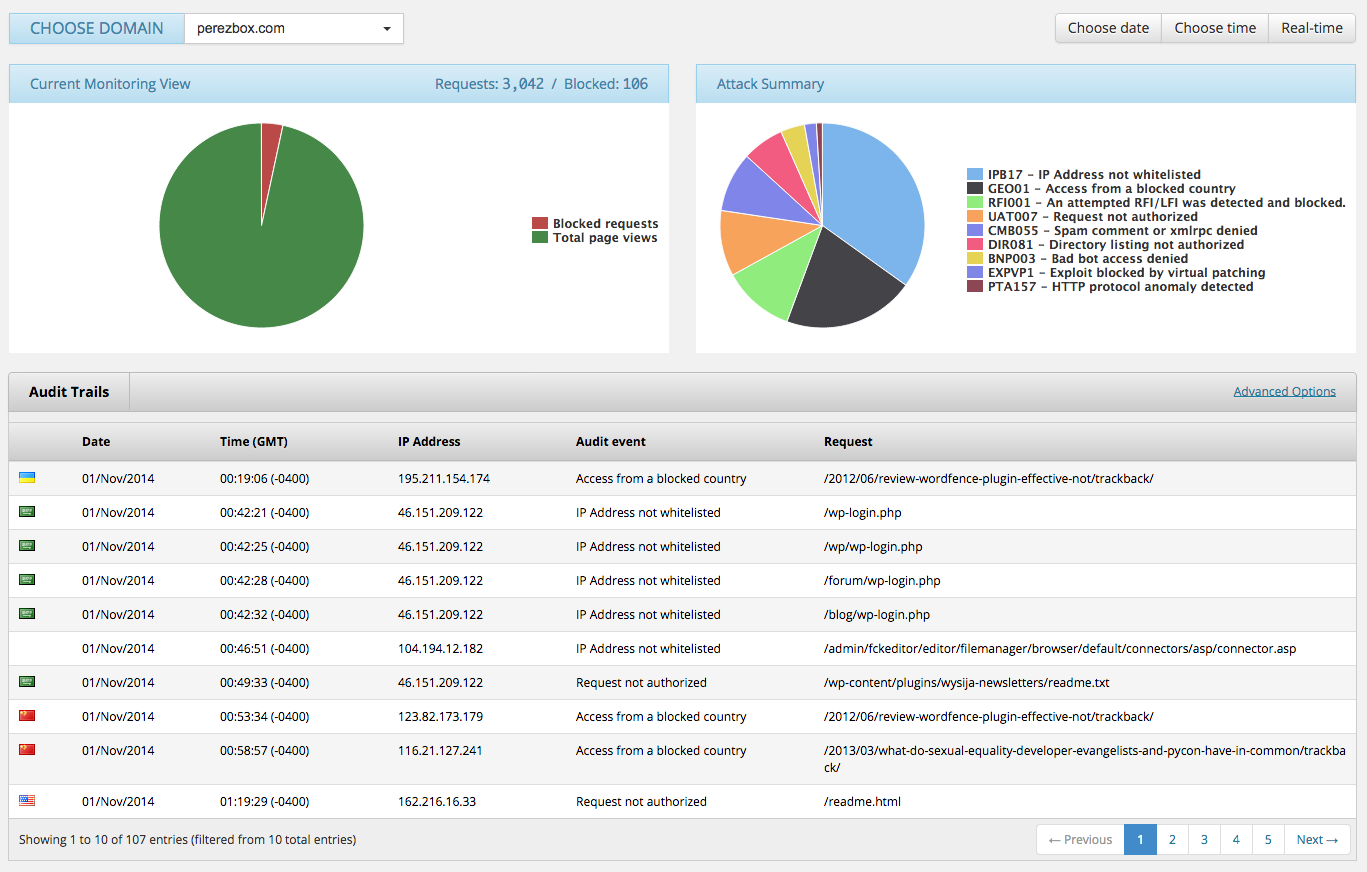
Unfortunately, monitoring is a reactive service. If it sees it, it notifies and I take action, and as nice a feature as that is, I have gone one step above that and added a protective layers on top of my website. This functions as a perimeter defense where I inspect every incoming request. It’s done in milliseconds, having no impacts on my website performance. I accomplish this by leveraging the Sucuri Website Firewall.
This Firewall inspects all incoming requests and ensures that only good traffic is finding it’s way to my server. This has additional benefits as it keeps my server costs minimal as I easily handle all incoming requests with little burden on my own personal infrastructure. With this firewall I’m able to deflect all of today’s attacks, include Brute Force Attacks, Denial of Service and more importantly Vulnerability exploitation attempts.
From this dashboard I’m able to take full control of what is and isn’t allowed to touch my website and server. I’m able to see all incoming attacks, create whitelisting rules and deflect them as I see fit.
3. Sucuri Website Backups
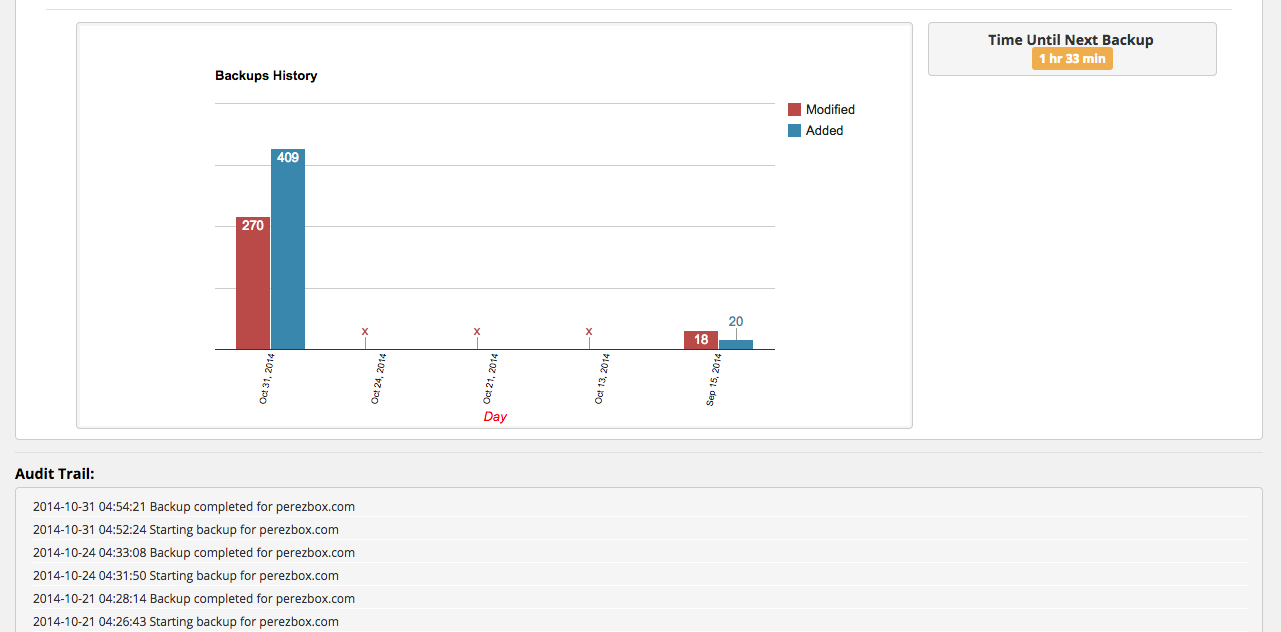
Last, but definitely not least, I employ a good backup strategy. I ensure that maintain daily backups, I never really know when I’m going to write or make changes. I also use a backup service to store all my data versus storing it myself locally or on my own server. There are a number of really good WordPress Backup solutions, I use mine because, well, we built it and I should.
Via my backups I’m able to see how often things are being retrieved and whether there are any errors. This ensures that if something catastrophic happens, say I get hacked and the cracker decides to delete my server I will be lost no more than 1 day’s worth of data (depending on time).
One can never be too prepared…
My Online Habits
In addition to the things I do on the server, the application and with the tools, I also practice good online behavior. By this I mean the following:
- I separate browsers by function to avoid CSRF type issues between social media an my platforms
- I disable JavaScript and AutoPlay for objects in my browsers
- I open links via Virtual Machines (probably a bit too excessively)
- I don’t open links in emails
- I rarely open social links on Twitter, Facebook and others – without scanning first at least
- I run an AntiVirus on my local machines
- I run a local Firewall on my local machines
I do all these things to ensure and avoid, where possible, any cross pollination between my environment and the properties in which I write on.
Day to Day Maintenance
I know what you’re thinking, after all this he’s got to be fine!!!, right?
Well, I’m not a leave it to chance kind of guy. Every day I go through a normal process of checking how all my websites and servers are doing, it doesn’t have to be long, but it’s a necessity.
- Is there any suspicious activity? High CPU usage? High data input or output?
- Any unrecognized crawls?
- Who is attacking me today?
- What kind of attacks am I seeing?
- Who is attempting to log in?
- Did my backups run?
- Did any files change? if so, why?
- Am I current? Up to date? Do I need to patch anything?
Sometimes, depending on what I find this could take longer than I’d like. Sometimes I break it into two times a day, just honestly depends. More importantly, I leverage all the tools at my disposal to ensure I have a complete picture, and use that to make the best decisions.
With this, I feel confident that when you are visiting my website you are doing so safely and that I’m taking all the precautions available to me to ensure your online experience.