Integrity Monitoring with Website Security
We spend a lot of time talking about the tools at our disposal to prevent hacks. Tools like security plugins, or cloud-based WAF’s, but we need to remember that security is a cyclical process. A comprehensive thought process forces us to be be considerate of all security domains – Protection, Detection, Response.
In this article I will focus specifically on Detection, more specifically the importance of integrity monitoring.
What is Integrity Monitoring
Integrity monitoring is a process of detecting when something changes in the environment. When a change is unauthorized it is typically indicative of a compromise.
FIM, as it is known, is a very common security control in large enterprises. Not so much with micro- and small- businesses.
FIM and Website Security
FIM technology is sometimes built into the security plugins for CMS’. I know that plugins like WordFence and Sucuri include it in their plugins for WordPress. But if you’re like me, and don’t like to run security in the application layer, you can use technologies like OSSEC HIDS (A free tool) to do the heavy lifting for you. My configuration combines OSSEC with Trunc, which I use to collect, aggregate and alert on events.
OSSEC has a syscheck daemon that will run at a set frequency and record changes as they occur.
Practical Example of FIM in Action
FIM is built on this idea that even with all the preventive controls at your disposal, the odds are you will get hacked at some point. This is especially true for small websites that lack resources, teams and knowledge. If anything, it makes FIM technology that much more important as it’s a failsafe in the event something does happen.
To demonstrate this point…
Most recently I was in the midst of some research:
- Part 1: How WordPress Gets Hacked in 2022 – Initial Reconnaissance
- Part 2: What Hackers Do with WordPress in 2022 – Post Hack Analysis
- Part 3: Analyzing 17,000 Spam Links on a Hacked WordPress Site
- Part 4: Hijacking a Websites SERP Results with SEO SPAM
- Part 5: Navigating 81 Layers of Encoding to Reveal the C&C
The research was designed to follow a bad actor as they made their way through one of my honeypots. One of the tools I used to monitor what they were doing was the OSSEC HIDS platform, specifically the FIM technology.
It would report changes like this:
** Alert 1662160965.3144148: mail – local,syslog,syscheck
2022 Sep 02 23:22:45 webhoney1->syscheck
Rule: 554 (level 7) -> ‘File added to the networktesting.net directory.’
New file ‘/var/www/[honeypot domain]/lyscide.php’ added to the file system.
To give you an idea of the number of changes they performed during the process. Here is a quick view of the number of time “rule: 554” was triggered in the past 7 days.
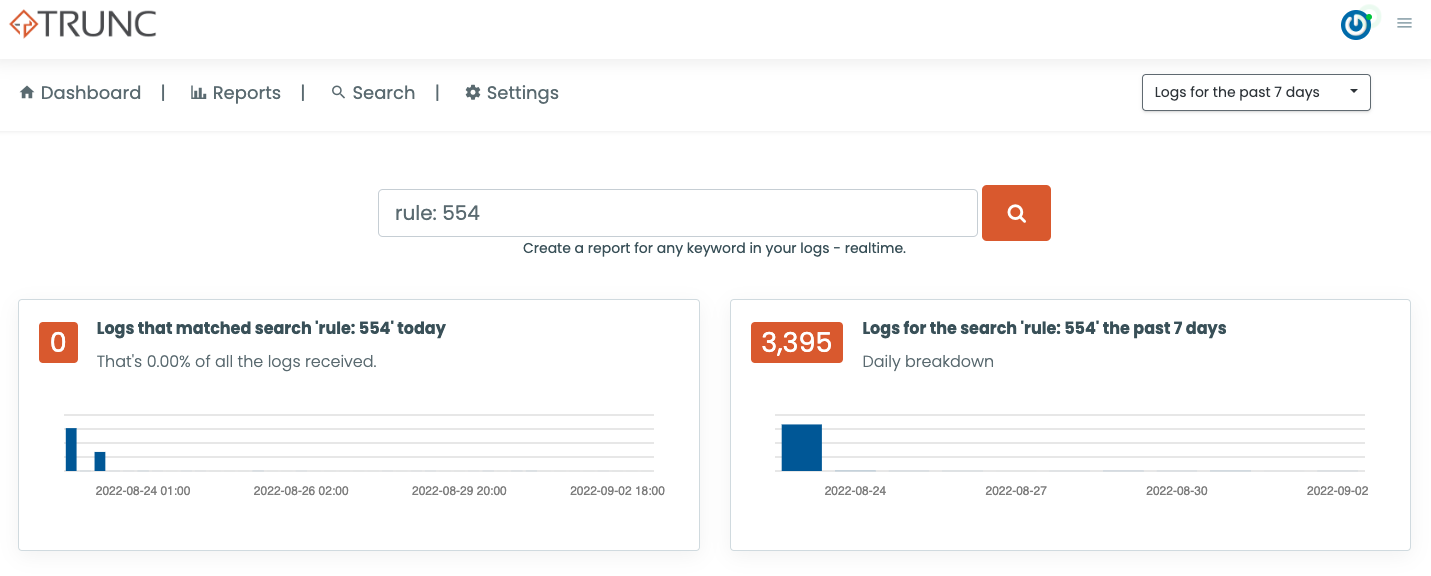
Every triggered event was the bad actor making a change, or adding a payload. Here is an example of the files being added:
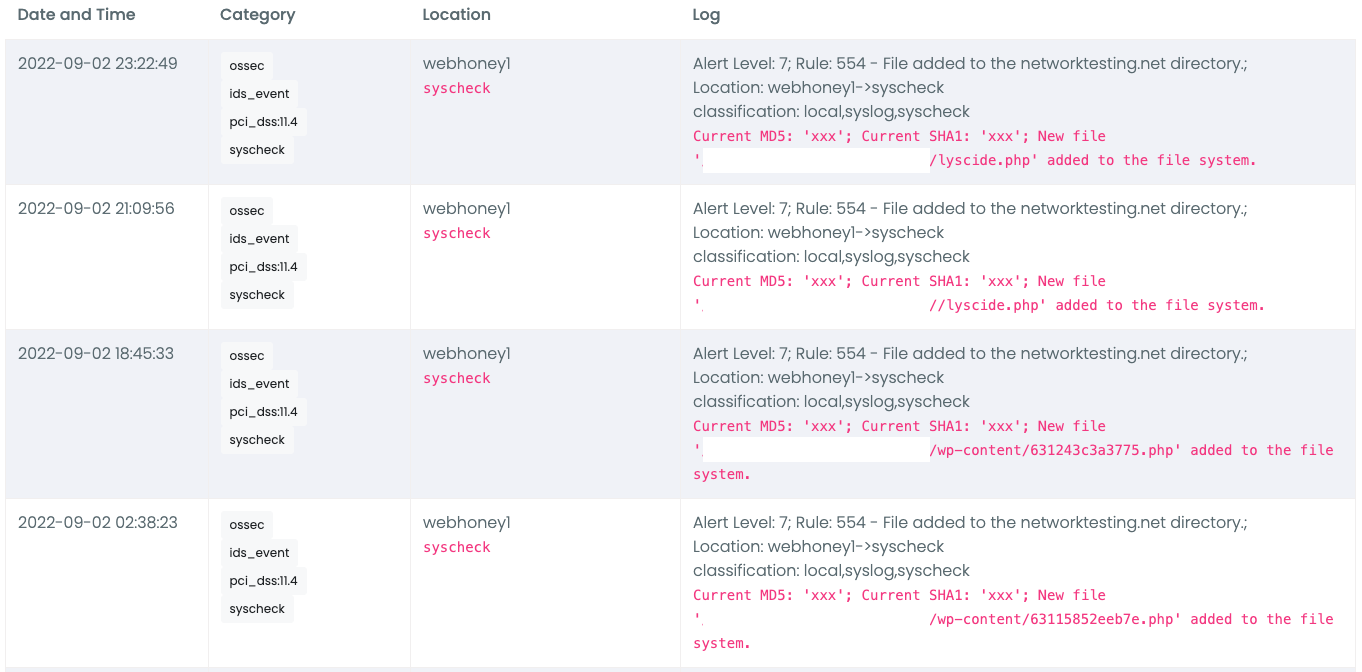
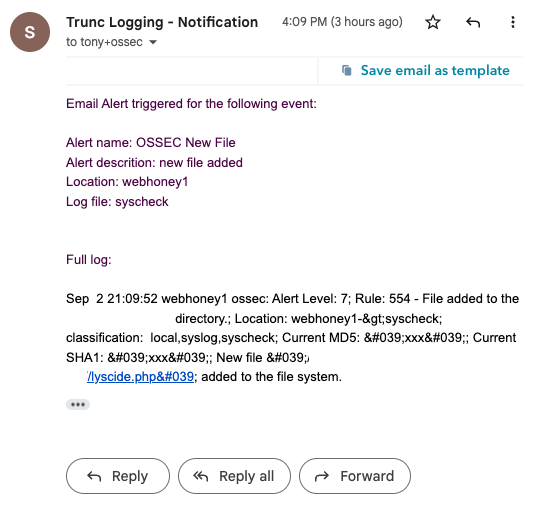
These events would then trigger notifications that would alert me to what was going on:
FIM and Website Security
As defenders we have the responsibility of being right 100% of the time, while bad actors have the luxury of only being right once. It’s because of this that I like FIM technologies. When implemented correctly, they can be an invaluable tool.
While the scenario above is a bit extreme for most, it should highlight how powerful it can be for websites administrators. The one big caveat is to make sure to disable it for directories that you expect a lot of changes in. For example, if using WordPress you wouldn’t want it monitoring /wp-content/uploads as it might be too busy (depending on the type of site you’re managing). Or, you can also tune it to notify only on specific files (e.g., PHP vs JPEG).
If nothing else, check the application level plugins you’re using to see if they offer some form of FIM technology. If they do, make it part of your normal process to check their outputs to verify things are as they should be.
