“You Must Contact Us Immediately So That Our Engineers can Guide You Through the Removal Process by Phone. Your Computer is Disabled”
This past weekend, I watched The Beekeeper. I knew nothing of it, but that it had Jason Stratham in it, which meant there would be some action scenes. It turns out that the premise of the movie is Jason taking revenge for the effects of an online scam where someone he cared about committed suicide after having her life savings wiped.
Being in tech, specifically cybersecurity, I was amused at the storyline and resonated closely with some of the things they discussed, specifically how scammers target and take advantage of susceptible audiences (i.e., Older populace, Young children, etc..).
Fast forward to Tuesday, January 24th, and I get a call from my mom. Her computer was making alarm sounds, and a warning told her she was compromised and had to call Windows Support to get immediate help.
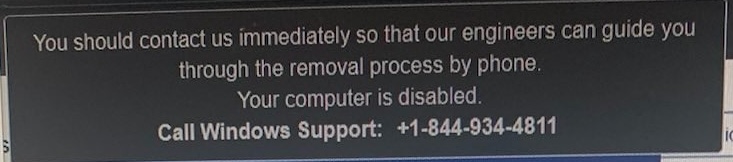
She called me when it happened, but I was on another call. I called her 20 minutes later, and sure enough, she had dialed the phone number. Below, I capture what the scammers did to try and win her over and what you should watch out for.
It also serves as a reminder that while we might be vigilant, we have those closest to us who might need constant reminders of the threats that lurk on the web.
Scare Tactics and Abusing Knowledge Gaps
The process is well scripted, and it’s easy to see why someone might fall for it. The scammers had American accents; we’re not talking foreigners in Asia, where it’s evident they are from somewhere else. They spoke well, communicated the problem clearly, and were patient as my mom was battling her nerves.
They provided information that appeared to be legitimate. They identified themselves as working for Microsoft and provided a work ID number to call and verify quickly. But who really does?
Kevin Thoomas
Employee ID - 1006
Online Windows Certified Technician
Phone: (412) 278 - 7624First they request access, and they use AnyConnect to gain entry to the device. They then proceed to focus on highlighting issues they find.
Device Protection Off
They open command prompt and run “manage-bde -status“
This outputs:
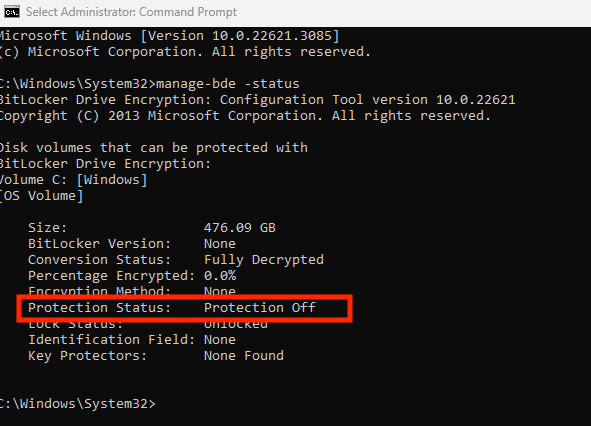
They then use this to emphasize how protection is off on the computer. Mind you, this looks explicitly to see if disk encryption is enabled—something most users never configure, especially at home. Because the device is not protected, they must get AntiVirus immediately, and they can help with that.
But to further showcase why it’s important…
Event Viewer Warnings
They open event viewer, navigate to the administrative events and highlight all the warnings in view:
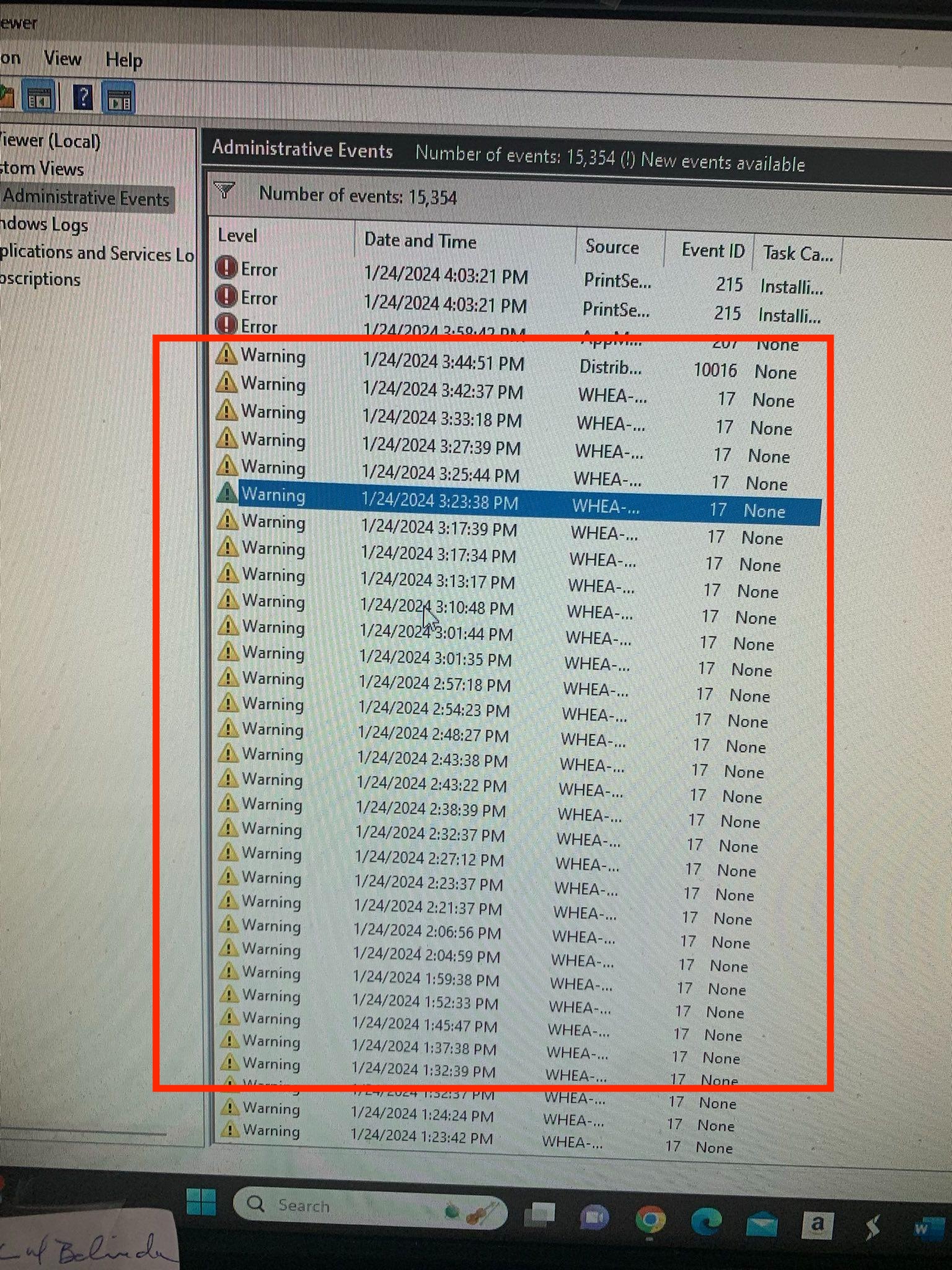
These are all the bad hackers trying to get in!
Actually, it’s an issue with one of the drivers and a known issue with Windows. But to the unsuspecting user, all these “Warnings” must be bad. Right?
Show Bad Connections
The icing on the cake to make the case is to show all those bad connection attempts by hackers trying to get into the machine. They did this by running “netstat -sp tcp” in the command prompt which generated this:
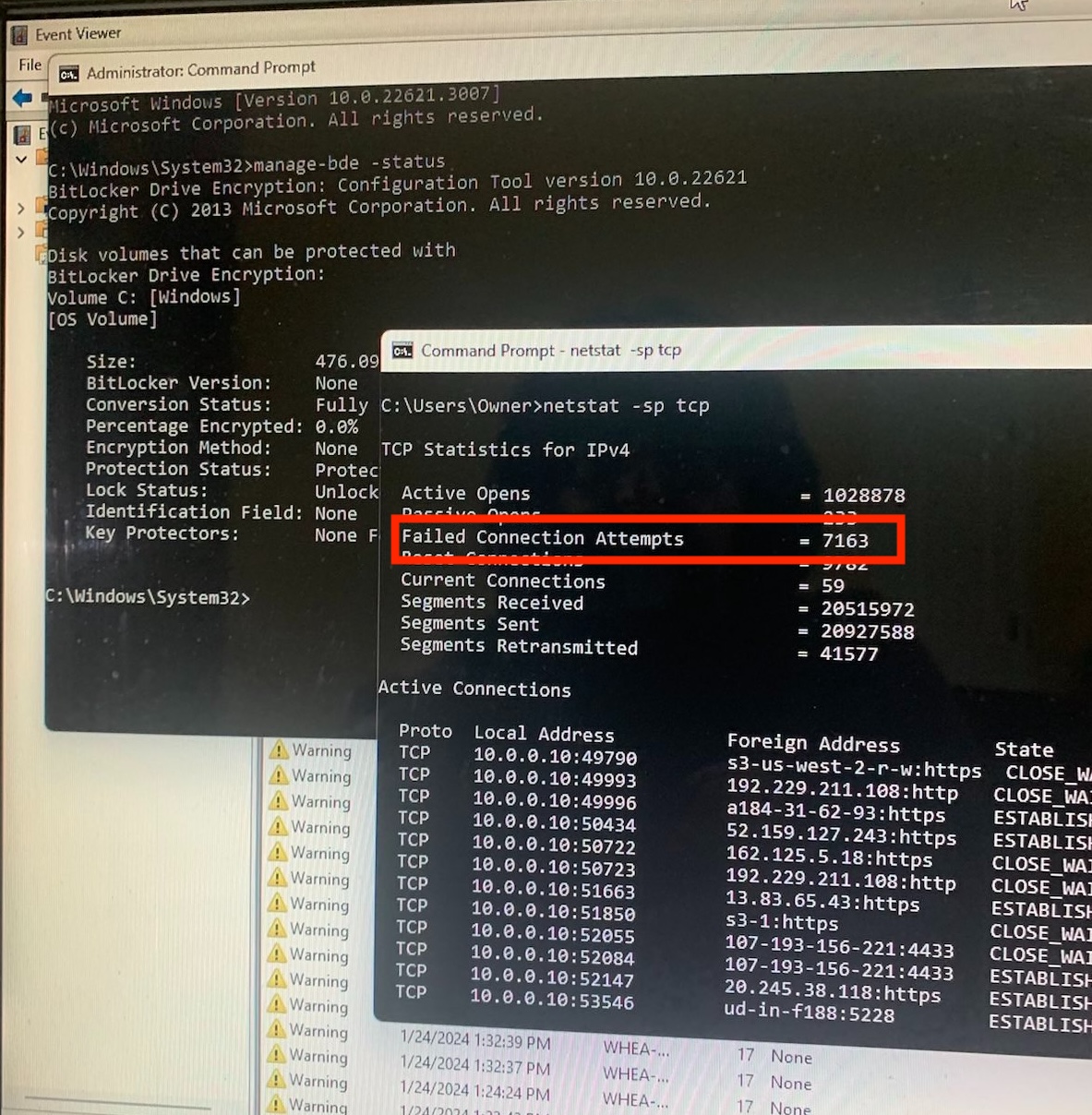
Here they show 7,163 failed connection attempts. You see, hackers are trying to hack you!
Coincidently, when I checked it again later this was a more realistic number:
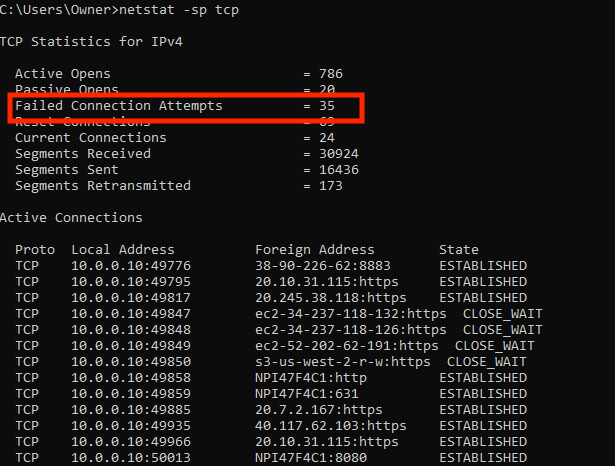
This is more in line with what I would expect.
What they were doing was initiating a bunch of failed requests with AnyConnect. If you logged into their Event Viewer, you could see all the failed Anyconnect connection attempts. They were creating their problem to sell a solution for it.
Educate Loved Ones of Online Scams
The scammer didn’t get very far outside of scaring my mom. She refused to give the scammers permission to make any changes until she spoke to me. She also took it upon herself to take pictures of everything he was doing to show me.
When we finally connected I had her shut off the computer until I could get there. This terminated their Anyconnect connection. Which was a good thing.
For whatever reason, they wouldn’t make any changes without her giving them approval. They opened notepad and asked her to write “AUTHORIZE” before they proceeded. For context they recorded everything via her notepad:

This tactic is very curious. I spoke about it with some colleagues, who said it’s because they want to come off as a legitimate business, and most people are so scared that they’ve built a bond with the scammer and typically say yes.
From there, they install an AntiVirus and take their credit card information over the phone. They seem to install a legitimate AV product and then make money off that conversion. There is also the issue of them having your card information. It could all spiral out of control very quickly.
Here are a couple of things to bare in mind to help you be a little more vigilant:
1 – Microsoft Tech Support will not call you to install an AntiVirus, they have their own built in solution (windows defender);
2 – If it is sounding alarms and has a big pop up screen, it’s likely just a scare tactic;
3 – Close all your browsers, and tabs, and see if it goes away. It’s likely nothing more than malvertising campaign where a pop up is used to scare you;
4 – Do not allow someone to remote into your machine that you are not familiar with;
5 – Don’t be fooled by nice sounding folks that have your same dialect (don’t call the number);
While none of these things occurred for my mom because she refused to proceed, it’s a reminder that we should always be vigilant online. Take a minute to educate your family, kids, parents and grandparents of the threats that lurk online and how to ensure they stay ahead of these types of scams and threats.
