Web Threats Are Real: Be Proactive
This post is really designed for my family and friends. I write it because in the business that I am in I get to see hear the detrimental impact web based threats have on people. I hear horror stories of lost data, the amount of information they have lost and the impacts it has had on them and their businesses.
I by no means will cover all the things that you should do, but it will help better situate your online security posture.
Good security posture is about risk reduction…
Understand that when reading this there are many variables that have to be accounted for when talking about protecting yourself and not everything is under your control. The web is such that we have grown accustomed to what it offers us and now we have to learn to adapt.
Be Weary Of Emails
Many of you get a wide range of emails and your first reaction is often to click on the link. While the web continues to be the number one distribution mechanism of malware, email attacks are on a rise. The latest reports tell us that spear phishing attempts, that’s what it is called, is on the rise. They often embed links to compromised website and carry a myriad of infections within those sites. Here are a couple of things I would recommend.
Take your mouse and hover over the link, don’t worry, the act of hovering won’t cause you much harm. Here is an example of a FEDEX scam:
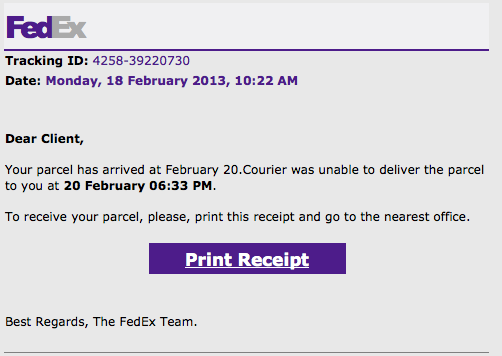
In this example if you hover over the Print Receipt button you’ll see that the site that comes up is far from FEDEX:
![]()
Here is a perfect example of a legitimate site being compromised to distribute malware, and the attackers using emails to lure people in. The take-away from this is treat every email as it’s malicious, even if they come from friends and family. If you get a random, unexpected email like this, you might want to send them a text or call and see what’s up and if it was intentional:
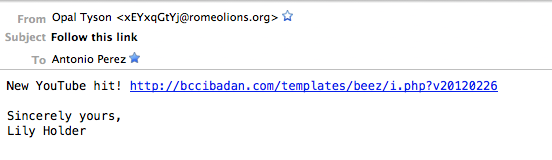
In this example it’s pretty clear that it’s malicious. The email name – xEYxqGtYj@romeolio…… – is the first red flag for me. The name of the link and file is another red flag. From this, I know it’s a Joomla site that has been attacked, and they’re leveraging the default BEEZ template. Granted, you probably wouldn’t know that, but by looking at it you could deduce there are a number of red flags with this engagement. Enough to hopefully raise some level of suspicion.
The real take away here is, if in doubt, don’t click. As I said before, the number of compromises is exponential these days, do what you can to protect yourself. The one thing that you can do to add a second layer of defense, in the event you accidentally click a link, is to disable JavaScript in your browser, but we’ll get to that later.
The Web Is a Beautiful, Yet Dangerous Place!!
You can love the ocean, but you must respect it as well.
Most of you surf the web without a care in the world. There was a time that maybe that approach was acceptable and tolerable, but those days are no longer here.
Making the mistake that today’s issues don’t apply to you is your first mistake. Second is not taking the appropriate precautions. I won’t go into a tangent on the subject but know that there are things that everyone should do if they spend any time on the web.
Disable Java
Java has had it’s rear end kicked this year. To the point that I am feeling really bad for its developers, but the reality of things is that it just hasn’t been a good year. It’s been the contributing attack vector to company’s like Facebook, Microsoft and Apple – that’s just in 2013; we’re only 2 months into the year.
The good news is that most of you don’t really need it installed for your day to day operations. The easiest thing to do is uninstall it. If you’re on Windows, you can follow these instructions: http://www.java.com/en/download/uninstall.jsp
If for some reason you can’t uninstall, your organization might require it for some reason, you want to do these two things:
- Disable the browser plugin until you require it
- Isolate the plugin into one browser and use that browser only when you need to leverage Java
You should also verify you have the latest Java version here: http://www.java.com/en/download/
Follow these instructions below to disable it in your browser:
- Firefox – Select “Tools” from the main menu, then “Add-ons,” then click the “Disable” button next to any Java plug-ins.
- Safari – Click “Safari” in the main menu bar, then “Preferences,” then select the “Security” tab and uncheck the button next to “Enable Java.”
- Chrome – Type or copy “Chrome://Plugins” into your browser’s address bar, then click the “Disable” button below any Java plug-ins
- Internet Explorer – Easiest way is to follow the steps here: http://www.java.com/en/download/help/disable_browser.xml
Disable JavaScipt
This one is bit close and dear to my heart. Many people will complain about this, and make arguments about how much of an inconvenience it is. Whatever the argument, the threat is real. I would argue that JS is the preferred browser based technology being exploited by attackers.
I should clarify that they are not exploiting the technology via vulnerabilities, rather by leveraging what it was designed to do. If you’re wondering what it is, just look at your favorite website. Think Facebook for instance. JavaScript allows half the functionality you enjoy and facilitates the cool user experience you love.
It’s perhaps the most popular browser based technology employed by most developers to improve the users experience. It comes enabled by default on almost every browser and doesn’t require any installs unlike ActiveX, Flash, and other similar technologies. I won’t get into the weeds on this and I’ll allow you to choose what you want to do, but if you are ok with a minor, temporary, inconvenience I recommend disabling.
This is how you go about doing just that:
Chrome
I really like the way Chrome allows you to quickly, and easily configure your JavaScript settings. The easiest way is to type this into your URL in the browser:
chrome://settings/
You can just copy and paste that into your browser and it should take you to the browsers settings page.
Click on:
Show advanced Settings...
Under Privacy click on:
Content Settings
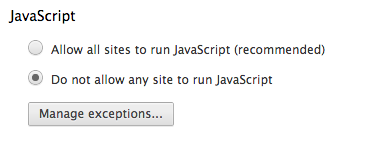
Scroll down until you see this and set it to what you see on the image:
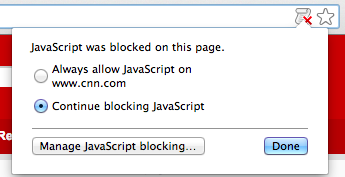
That’s it, now when you navigate to a site that requires JavaScript you’ll see this in the address bar:
If you trust the site add it to your exceptions and go about your business.
What I dislike most about this is that it adds the exception for good, you’d have to go in and go through your managed exceptions to remove sites as required. That can be a bit annoying. If you’re wondering why I would do that it’s because even known good sites get compromised, see my post on NBC’s compromise about two weeks ago.
That being said, this is still a good step to take. What I do is I use one browser with JS fully disabled and add exception for a very small list of sites I know are good and well maintained. All other sites that I have to visit that require JS enabled are done on a separate browser all together. I usually like using Firefox as the secondary browser. When I do this I try not to visit many sites or open other tabs, the idea is to reduce the potential risk of cross site scripting and or cros site request forgery attacks. When you do this with the guidance below on what to do on FireFox it’s a pretty solid solution.
I don’t expect most of you, if any, to actually do this. But do realize you have options.
One other, very feasible option, is to use VMFusion or VMWare and run browsers in Unity mode. This will allow you to run the OS you are most comfortable with and run the browser from the virtual machine (VM). In this instance if you get a download attempt or accidentally get infected it affects your VM and the box you’re using for every day tasks. But I digress, this is a bit more for those paranoid few..
FireFox
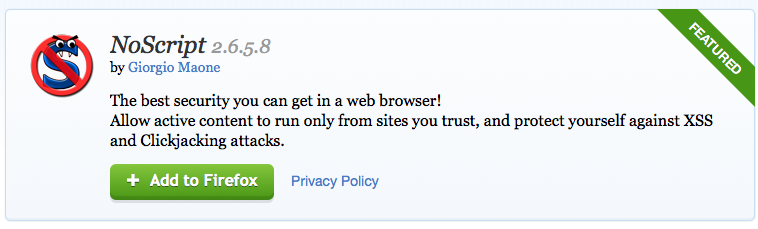
If you use FireFox, the easiest thing to do is install the NoScript plugin. You can try doing it via your settings, but it is less than user friendly and adding exceptions is a pain.
Here is the plugin:
Open the link from FireFox, and you should be greeted with this page when you visit the site:
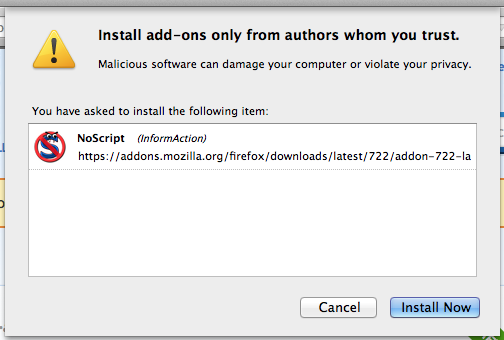
Click on the Add to Firefox and when its ready you’ll see it give you the option to Install:
You will need to restart the browser, so be sure you do that before proceeding. You can restart by simply forcing a quite or closing out your browser.
When it’s installed it will be activated by default and if you go to a site you know you’ll likely see the yellow bar I’m showing in this image:
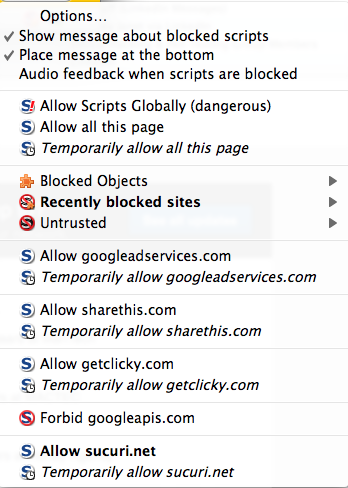
This is where I really like the Firefox option for handling sites that require JS to get anything done.
If you click on options You’ll be greeted with a dialog that shows you all the various JS objects trying to run. You’ll have to option to allow the entire domain, or allow specific JS objects. If you’re anal and paranoid, you’ll like this option:
If you combine this with my approach above it works well. It allows me to run JS on websites but allows me to verify what it’s loading and what I want to allow. If everything looks good I can add an exception for the current session.
Internet Explorer
Yeah yeah, I know that half of you still use Internet Explorer for your daily browsing needs. While I would encourage you to switch, I realize it’s unlikely. Note that my recommendation for IE is simply because it’s such a large target, I am not saying it is more or less safe, just that it’s a preferred target for attackers. I personally don’t like that, and prefer not to put myself in that situation.
That being said, knowing that you do, here is what you need to do.
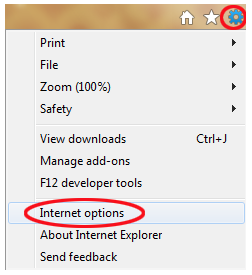
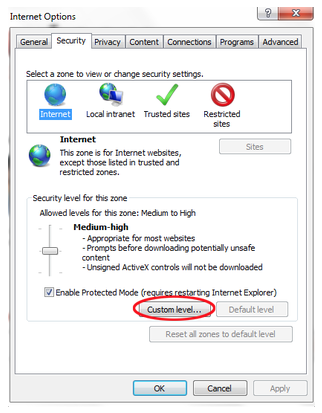
Navigate to Internet Options, you’ll do this by opening your browser and clicking on File:
Click on the Security tab on the dialog that opens and click on custom level:
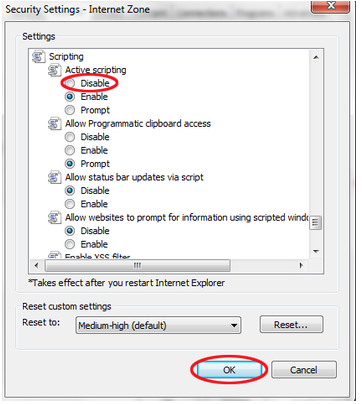
Now scroll down in the new dialog and find the area that reads Scripting and change Active Scripting to disabled:
Just like, done sir done. I don’t run IE locally so I’m a bit unclear on the way to manage the exception, but I assume it’s as challenging as FireFox’s built in mechanism.
As for the other browsers, they each have their own approach to handling JS I would encourage you to do a Google search.
Stay Calm and Surf!
If any of this scared you, I do apologize for that, but I assure you that if you take a deep breathe and reread the post you’ll hopefully find that it’s not that mind boggling. Follow the instructions, after dealing with the momentary mental breakdown that will ensue, and force yourself to maintain a better online security posture. This is a very high level cursory discussion on a few things you can do, but I recommend you take notice and apply what you can. If large organizations are falling victim to attacks I assure you that you are just as, if not, more vulnerable.
There was a time that wearing seat belts while driving was nothing more than a recommendation and very few folks applied it. The cars got faster, the accidents more menacing and now wearing seat belts is second nature to many. It took time and required a change in the way we think. The impacts of today’s web threats, although not as physically impactful as a car accident, carry with it huge life-altering challenges for us all and will carry similar changes int he way we think and interact with the web.
Take the proper precautions and surf smartly.
***Updated: March 7th, 2013***
I just came across another good post by Jeremiah Grossmon, Founder and CTO over at WhiteHat Security. If you’re not familiar with them you should be. In his post he provides some more very awesome guidance that we should all be adhering too, and the kicker is it’s simple to apply. Take a minute and read it here: http://blog.whitehatsec.com/tips-for-not-getting-hacked-on-the-web/


Thank you Tony. FireFox seems to be your preferred browser — yes?
Actually, no. I use Chrome more than I use FireFox. After a while Firefox seems to get bloated and starts having performance issues. Where I like FireFox is when I want to view sites I don’t trust but need to run JS. I can then use NoScript to enable and see the JS running and disallow those elements that I don’t trust. From an everyday browsing perspective it’s Chrome, from a selective viewing it’s FireFox. Hope that make sense.
Thanks for stopping by.