Phishing and Ransomware Leads Security Concerns for Organizations
The SANS Institute recently released their 2017 Threat Landscape Survey: User on the Front Line in which they interviewed 263 IT and security professional on the things that keep them up at night. Survey was conducted in May / June of 2017, it’s no surprise Ransomware was top of mind (e.g., WanaCry and Petya dominated the media). I am constantly amazed at the continued impact of Phishing threats.
This survey helps provide a deeper appreciation for what the security domain is faced with, while also providing insights into what the SMB market should be aware of (but are often not). This specific audience is technically capable, with a vested in interest in security as it’s their job (i.e., security / IT professionals), and it stands in stark contrast to the SMB market.
Insights Into The Threat Landscape
Over 70% of the respondents saw Phishing attacks, and 50% found some form of spyware. The most interesting tidbit for me was the assessment of it’s relevant organizational impact; where phishing had an impact of greater than 30% and spyware had less than 10%.
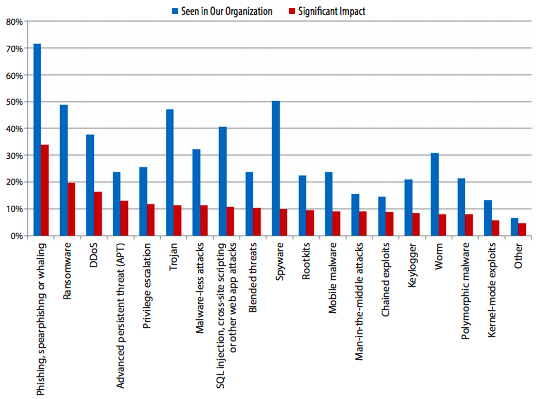
This is interesting because of the disproportional relationship between threat and impact. It has the potential to breed, and contribute, to bad behavior. If we start to attribute less impact to specific threats we run the risk of reducing our overall security posture. Yet, in many ways it’s an undeniable fact. It’s an interesting way for an organization to think through their risk position.
This also speaks to the fact that not all threats are created equal. A question was posed that makes me really sit back and wonder what it’s implications are, “Does that mean there is an acceptable level of compromise?” In many ways, you could argue that there is and our SMB customers recognize this fact.
Another interesting insight was around malware-less attacks, where 32% of the respondents reported experiencing it, with credential compromise or privilege escalation being the most impactful of the threats.
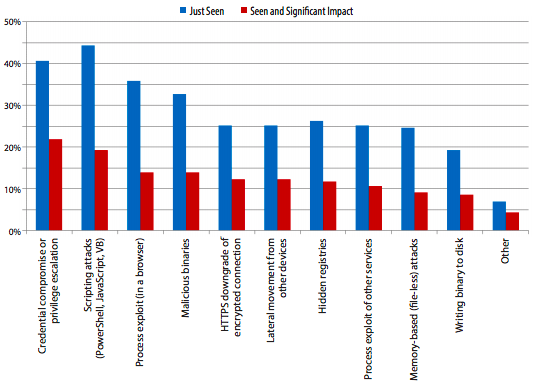
I was especially interested to understand the specific vectors being exploited, they were able to shed some light on this.
The two leading vectors being abused were Email Attachments / Links (74%) and Web-based Drive-By or Downloads (48%).
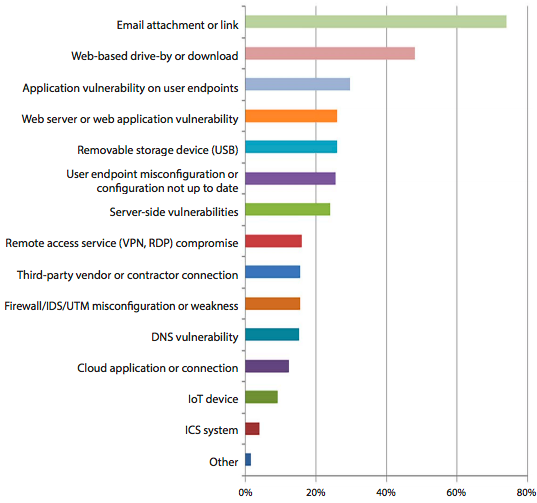
I focus specifically on the website security domain. It speaks to the greater relationship service providers (i.e., Hosts, MSPs, etc..) have in offering their customers secure environments in which website owners can be better stewards of the greater internet security ecosystem.
Insights Into the Tools Being Employed
Beyond the threats being employed and vectors being abused, I was particularly interested understand the the tools being leveraged to detect the threats.
The top 5 methods of detection revolved around human interaction, monitoring and logging. These were leading approaches by all respondents, and speaks volumes to the role end-uses play in their own security. It also places emphasis on the most under appreciated security function – monitoring / logging.
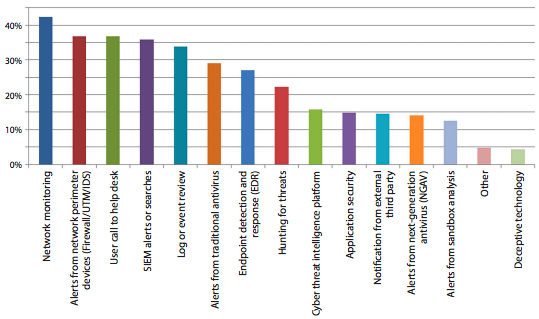
Our Responsibility as Service Providers
The big question is what can we as service providers be doing to better empower our SMB users?
Reports like the one SANS provided are interesting, but if these are the things organizations with resources are facing, what can be done to empower those organizations that don’t have resources? Not having resources is not an indicator of whether these are problems you should be concerned with, these are things that exist regardless of your investment to understand them.
I’ll be speaking on this very subject at the World Hosting Days in Vegas, September 12th. Join me in the conversation.
