HTTPS Does Not Secure Your Website
Ever since Google made their announcement that they were exploring the idea of using HTTPS as a Ranking Signal for your SEO, the web has gone nuts for HTTPS. For a number of security professionals it’s generated groans and a heightened level of annoyance and consternation at what has become an over abundance of irrational thought, perspective and improper guidance and insight.
To be clear, I’m not against HTTPS. I believe it’s a critical technology that should be employed when needed, but what I dislike greatly is when it’s used in the context of securing your website.
What is HTTPS?
Hyper Text Transport Protocol Secure (HTTPS) is the secure connection protocol for HTTP, the connection protocol we all use to navigate the World Wide Web (WWW) (i.e., it’s how we navigate between websites via your browsers).
A great illustration of the differences between HTTP and HTTPS is seen in the illustration below, provided by Comodo:
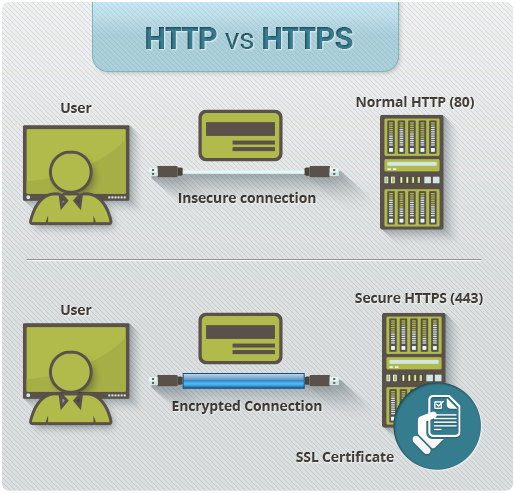
One could venture to say that the confusion all begins with the use of “secure” in the protocol name itself, it however does not mean the same across the full spectrum of security. In the instance of HTTPS, secure implies an encrypted connection between the browser and the web server. This ensures that the data traveling between your browser and the web server is safe by making sure that unintended users are unable to intercept the traffic.
There are obvious instances in which this type of secure connection is a must.
- Transfer of Personal Identifiable Information;
- Transfer of transaction data in e-commerce;
- Transfer of any other sensitive data;
Additionally, HTTPS makes use of two separate encryption protocols SSL (Secure Sockets Layer) or TLS (Transport Layer Security). Today, the preferred secure protocol is HTTPS over TLS; SSL was the precursor to TLS. More details on this in another post.
How Does HTTPS Not Secure My Website?
HTTPS is a mechanism for securing information in transit. It ensures that the information being transferred between a browser and web server is safe from what is known as an Man In The Middle (MITM) attack. This however is a very small piece of securing your website.
The actual act of securing a website is a very complex process. HTTPS does not stop attackers from hacking a website, web server or network. It will not stop an attacker from exploiting software vulnerabilities, brute forcing your access controls or ensure your websites availability by mitigating Distributed Denial of Services (DDOS) attacks.
Here are a number of articles I’ve written that better explain the dynamic nature of securing your websites, and what happens when you don’t. Notice how HTTPS has very little to do with the process.
Even when looking at HTTPS specifically, things like downgrade attacks exist and as of late we’ve seen a number of vulnerabilities targeting SSL / TLS protocols. Vulnerabilities like Heartbleed, Poodle, and LogJam to name a few of the popular ones. Those however, are discussions for a different day, and for the purposes of this post it’s enough to understand that encrypting information over HTTPS is definitely a good thing.
I am not one though to believe that encrypting everything is a necessity. For most things, I find it unnecessary. There have been a number of explanations given for why securing all communication is important, some more valid than others.
Below are the top five (5) reasons I see for how HTTPS secures your website and my thoughts on each:
1. Authentication
Of the many reasons people believe HTTPS provides a secure website is around the idea of Authentication. The idea that with HTTPS you are now able to authenticate the true owner of a website. The idea behind this comes down to how Certificate Authorities (CA) work. CA’s are the entities responsible for providing verified certificates used in HTTPS connections. They are the little green boxes you see in your browser when a website has HTTPS enabled.
You can see what it looks like in the following image.
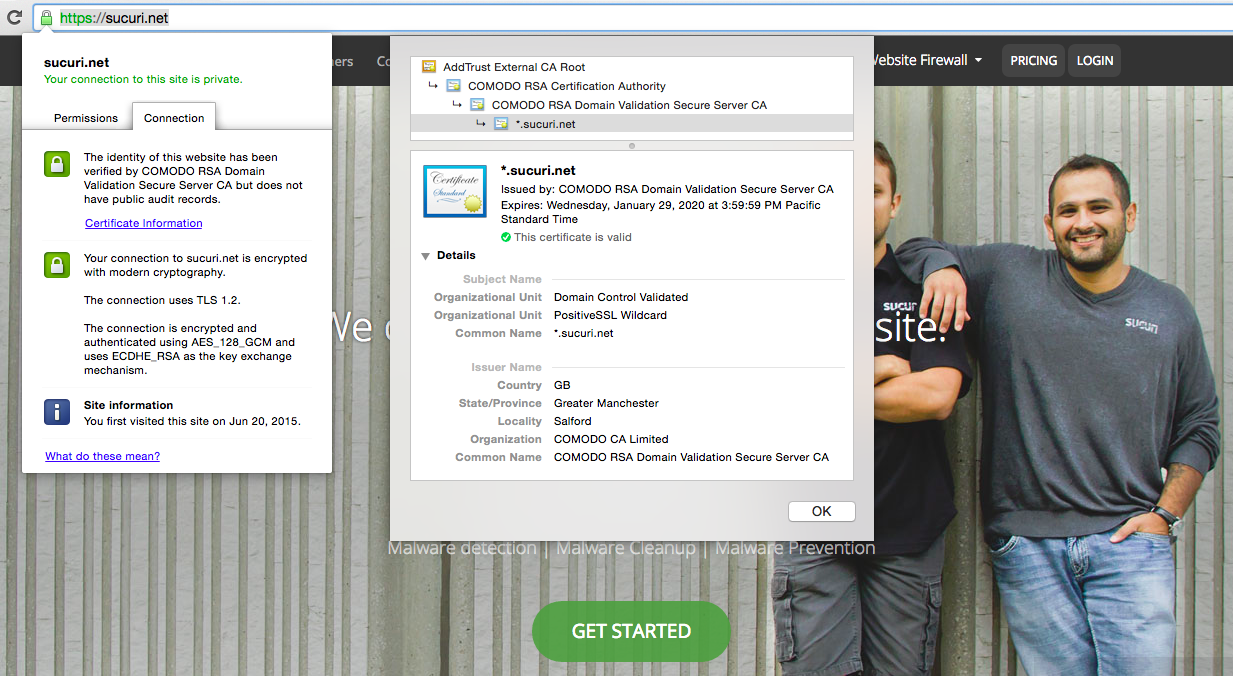
Sample Green Padlock in Browser and Certificate Information
As you can see, if you click on the green pad lock it gives you more information about the certificate. Information like who issued the certificate, COMODO RSA Domain Validation Secure Server CA, and the type of secure protocol being used, The connection uses TLS 1.2.
This does little in the form of Authentication. What it does tell you is that the web server distributing the website is authorized to do so, but it doesn’t confirm that it’s authorized to do so by the domain holder.
The authentication argument is based around this description:
A proper SSL certificate also provides authentication. This means you can be sure that you are sending information to the right server and not to a criminal’s server.
Contrary to popular belief, when subscribing for a certificate (unless a large, recognizable entity) one does not have to provide much in the way of corporate documentation. In fact, often the authorization comes in the form of an email sent to something like webmaster@yourdomain.com. Confirm the inquiry, and you’re accepted as the authorized domain holder.
To prove this point, you can see various examples in recent history in which several entities had their certificates spoofed. In 2014, Threatpost reported that a number of popular entities were having their certificates spoofed:
Dozens of phony SSL certificates were discovered this week mocking legitimate certs from banks, e-commerce sites, ISPs and social networks. If a user stumbled over one of the bogus certificates on a mobile device it could put them at risk for a man-in-the-middle attack.
Disguised as official certificates from Google, Facebook, GoDaddy, YouTube and iTunes, just to name a few, the certs aren’t signed, so it’s unlikely they’ll dupe anyone using a conventional browser.
The very important sentence in that quote is the last one – the certs aren’t signed, so it’s unlikely they’ll dupe anyone using a conventional browser. This, unfortunately, is the wrong assumption. Being I work with consumers and endusers on a daily basis, there is one thing I have learned. Everything I ever thought I knew or expected to be common knowledge is wrong.
I do want to state that there are instances in which organizations employ certificate-based authentication. In these instances organizations do in fact use the certificates to allow the visiting user to authenticate with the environment. These are not the instances I’m discussing above.
2. Integrity
The argument is that because it’s now over HTTPS, and you’re protecting against MITM attacks you can be assured that the information is in fact the information you’re meant to get.
This is incorrect.
Yes, if someone is able to control the flow of traffic on a network, they can definitely manipulate the integrity of the information being displayed by intercepting the traffic via a number of tools. This always sucks, and yes, HTTPS will assist, as long as the attacker doesn’t have full control of the network; which in that case it’ll do little to provide any assurances. More importantly however is when a web server / website is compromised. If compromised, the attacker can manipulate any of the contact and HTTPS will do little to stop the manipulation of the information the website owner intends to share.
What HTTPS will do is deliver the intended information securely, good or bad. HTTPS is indifferent. Everyday we work feverishly to clean infected websites distributing malware. In none of the cases did HTTPS do anything to ensure the integrity of the information being displayed. What HTTPS did do though is deliver the manipulated information to the unsuspecting website visitors, securely.
3. Encryption
Hard to argue the importance of encryption. I bet you every CEO recently affected by the latest data breaches wishes they’d had placed a bit more emphasis on it as they enjoy their unplanned early retirements. That brings us to a different point when talking encryption.
The argument with Encryption and HTTPS is that it encrypts the information as it’s being transferred from the browser to the web server. This is known as encryption in transit, and talks to nothing about encryption at rest.
Encryption at rest talks to how the information is stored once it hits it’s final resting point – the web server in which the website is housed. Again, based on my experience, rarely do we see encryption traverse the entire information lifecycle. Website owners will encrypt the information in transit, then store it decrypted at rest. We’ve seen this time and time again by organizations like Target, Home Depot, LinkedIn, Sony and so many others. If the largest of organizations are incapable to understand the concept, then I can assure you the point is lost on everyday website owners. Worst yet, no one ever talks about the importance of encrypting information in transit.
4. Protects Against Phishing
Phishing is a technique employed by attackers in which they can emulate a legitimate website and use it to steal information, often attributed with a social engineering attack. You see them sent out via emails, but they can also be seen via social media outlets.
The user clicks on a link and they go to a page that resembles something they expect, something like Facebook, Twitter, or their preferred bank (depending on the region). Sounds silly, but highly effective.
The argument here is that via HTTPS, the website owner is assured that they are going to the right website owned by the right party. In a perfect world, this would be correct. In the world we live in though, it’s incorrect. Not because the certificate doesn’t verify the owner – it does. The problem though is that if the website housing the phishing page has https, and it is verified, it will show the user that lovely green padlock.
The expected rebuttal to this last statement is that the user would click the pad lock, verify the source and know that it’s verified to the wrong entity. While true, in terms of expected response, it’s unrealistic in terms of how endusers interact online. As an example, when was the last time you actually noticed the pad lock? Then ask yourself, when was the last time you clicked the pad lock and looked at the certificate information? While some will obviously say it’s part of their routing, I can assure you that is the 1%.
Everyday users see the padlock and trust everything else from there, even if it’s from a different domain.
5. Nation State Attacks
Since the Edward Snowden disclosures every one has been buzzing about privacy. All of a sudden, everything we feared was happening but never had proof of came to light. With that has come the shock and awe of such revelations, specifically those of our governments spying on us and everyone else for that matter.
I honestly don’t even know where to begin here.
With the latest revelations, I can’t help but think that nothing is secure from nation states. I somehow can’t imagine how HTTPS is going to magically stop the spying of anything. I also can’t help but imagine that outside of security circles and the media, the average user is either oblivious to the revelations and how it impacts to them or care enough to do anything about it.
My advice, assume everything you do online – HTTPS or HTTP – is being monitored.
Securing Your Website is Important
I am obviously a huge proponent for securing your website, and while important, HTTPS is not the key. It’s definitely a critical piece of the overarching security wheel associated with website security, but it’s not going to stop websites from getting hacked, the distribution of malware or keep website owners safe.
It will continue to be a critical piece to ensuring information in transit is protected from attackers, but that’s the extent of the secureness it’ll offer your website. We do have to start talking about encryption at rest, in addition to encryption in transit. If we look at the number of data breaches, HTTPS did little to stop the exfiltration of data.
Additionally, remember that HTTPS will have other detrimental impacts to both security and your business as a whole. One of the biggest things I don’t see anyone discussing is the fact that HTTPS not only blocks the bad guys, but the good guys as well. This means that most of the modern Intrusion Detection / Prevention Systems are also blocked from analyzing the incoming data – it’s encrypted. This is not a reason not to employ HTTPS, but it is a point that you must take into consideration.
I have no doubt that HTTPS will continue to grow in popularity, and I’m okay with that. What I take exception to though is when technology professionals say that one of the driving factors for HTTPS is it’ll secure your website, because it won’t.
Note: If you find yourself deploying LetsEncrypt, here is a simple guide to help you in the process.

Thanks for the article, Tony. I suspected as much but it’s great to have your information in an easily understood format. :)
No problem @Mizagorn:disqus
I get your point – there’s a lot of hype.
Does anybody that really knows what they’re talking about say that “one of the driving factors for HTTPS is it’ll secure your website”? Where are the people in the know who actually say this?
And depending on your perspective, yes, it can secure your site. You just have be specific about it – much in the same way that you’re specific about how it doesn’t. E.g. WordPress – if I’m an admin my “session” is stored in my cookies. If I don’t use HTTPS those cookies are visible in transit. So yes, in this specific case “HTTPS secures my website”.
Hey @paulgoodchild:disqus
Hard to say, I would hope that if they know what they’re talking about they wouldn’t, but every day I’m surprised. Sometimes it’s a fundamental lack of understanding. There is also a difference between knowing and thinking you know, and worse figuring out where one fits.. :) So to your rhetorical question, I’ll keep an eye out…
Sure, we can get into a discussion where we fight over semantics and split atoms.. but the truth is, like I say in the article, security of the website is fundamentally different than securing data in transit, which is what is what it does by design. The real problem comes down to the interpretation by the masses that by leveraging SSL/TLS they are now secure. So while we debate these esoteric topics website owners that have been misinformed are getting hacked.. : /
Thanks for stopping by.
Tony
I don’t really get the rant. HTTPS is one piece of the puzzle, nothing more. I think it is a good thing, if a hype gets more people to set it up for their site. So many users log into their website while using a public hotspot. In general I would never consider a network secure nowadays anymore. So encryption in transit should be the default.
Hi @j@jeffshaders:disqus
If you don’t get it, it’s likely not something that you deal with on a regular basis. The problem with the noise is that it’s misleading and it fosters a general distrust in the technology. The post is designed to talk specifically to how HTTPS does not secure your website, which is an important point for most of the website owners I specifically engage with. Whom, for whatever reason, believe that by using HTTPS their website is now secure.
Thanks
Tony
Useful article. Thank you.
very good article, question, when I installed my WordPress website I used http and not https. Do I need to reinstall the entire site again or is there a way to convert to https after you have installed and setup a site?
No, you don’t need to reinstall the site.. you simply need to reset so that you’re accepting HTTP requests and fixed your mixed content warnings… I speak to it in the post I wrote here: https://blog.sucuri.net/2016/04/troubleshooting-mixed-content-warnings-https.html