DNSChanger Malware: Verifying You Are Clean
There has been a lot of buzz this week about the DNSChanger malware, I wanted to take a minute to summarize it for my friends and family.
History
If you’re curious what this is and why it is so important then read this section.
What’s important to note is that DNSChanger is a type of malware. Its been generalized in all the discussion, but there are a number of variants out there. For instance the group that was arrested, that has led to all this commotion, were distributing a number of variants: TDSS, Alureon, TidServ, and TDL4 viruses.
As for some history, back on November 8th, 2011, the FBI and Estonian police arrested a number of cyber criminals under an effort titled Operation Ghost Click. The challenge here became the cybercriminals had put in place a number of their own DNS server. For those not familiar, these DNS server are what allow you to interact on the internet. They are, for lack of a better word, your gateway to the interwebs. This was important because once they were able to infect your local computer with the virus, it’d traverse its way to your router which would then modify your local DNS settings. This would then point your machine to one of the malicious DNS servers. To you, it was probably unnoticeable, you’d still visit your webmail and your favorite social networking sites (e.g., Facebook, G+, etc…) but from time to time you’d find yourself on pages selling you things you weren’t looking for. This was done because they would make money on the click throughs, in this little effort they made something in the neighborhood of $14 million
I won’t get into what a DNS server is, but you can find good reading material on the web. I personally like the How Stuff Works website for how it breaks things down into a simple to understand manner. In this instance its no different, they provide you a good article titled, How Domain Name Servers Work that explains how it works better than I can ever dream to.
After the raid though, the FBI and their partners assumed control of these DNS servers. They purged the servers to ensure they were not maliciously distributing adware or any other malware types and added them to the existing DNS server lists. The issue here became that in most instances these DNS servers are owned by internet service providers (ISP) – e.g., Verizon, AT&T, Comcast, etc.. In this instance, ownership was turned over to the Internet Systems Consortium. As you might imagine owning infrastructure costs money and finally under a court-order, the ISC has been directed to shut down these servers.
Internet Systems Consortium is the renowned producer and distributor of Critical Internet Infrastructure software. Source: ISC.org
This is where we find ourselves today. Under the court-order, July 9th, 2012 is the date these servers will be shut down. At its peak, I believe the infection had impacted about 300 – 600 hundred thousand computers. This number is drastically less now, I think the latest estimates had it less than 50 thousand computers. Its definitely not the Internet Doomsday you might have heard about on the news this past week, so rest easily.
That being said, its still something you want to check because if you’re one of those 50,000 or so folks that find yourself not being able to update us all with what you ate recently or the gritty details of your love life you might find yourself devastated on Monday.
What To Do
So let’s get this going, what can you do.
Step 1. Ensure your Local AV is Up to date
Go to your local Anti-Virus, find the update option, and run a fulls can of your machine. The idea is to ensure that the virus is not resident on your machine.
Step 2. Make Sure You are Directing Right
The ISC has put out a very simple page to verify if your internet traffic is directing correctly, they have set these up globally, but for those in the states you can go here: DNSChanger Check-Up For those out of the country you can find other similar links on the FBI DNSChanger Resource page.
Yes, nothing fancy about the page, but its simple, RED is BAD and GREEN is GOOD.
This is only the first step though. This only means you are directing on the web fine, it doesn’t mean that your DNS server settings aren’t configured correctly on your machine.
Step 3. Check That DNS Settings are Good
Fortunately the FBI was nice enough to put together a nice little breakdown of what to look for, you can find their report here: http://www.fbi.gov/news/stories/2011/november/malware_110911/DNS-changer-malware.pdf. Note that this is a PDF and might try to install if you click, its ok.
I’ll provide you a quick checklist of things you can do in this section for Windows and MAC.
Windows Users
Easiest way is to open your command line and check your configurations, this is the easiest than trying to write out all the various windows you have to open and navigate.
- Open Start menu
- Type cmd into the box labeled “start search”
- Press enter
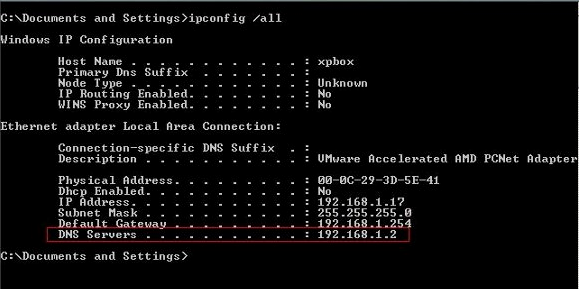
- Type ipconfig /all into the black screen
You should see something like this:
Take the IP next to the DNS Servers title (highlighted in the red box) and type those numbers (a.k.a IP) here: https://forms.fbi.gov/check-to-see-if-your-computer-is-using-rogue-DNS.
This will tell you if that DNS IP is part of the DNS servers being shut down.
If you are set to Obtain DNS Server address automatically and you think you could still be at risk you could switch your DNS to use Google’s public DNS until next week sometime. Their DNS server IPs are:
- 8.8.8.8
- 8.8.4.4
MAC Users
You’re in luck, its even easier for you.
- Click on Apple menu icon
- Navigate to System Preferences
- Click Network
- Click your connection, it’ll show in GREEN
- Click Advanced
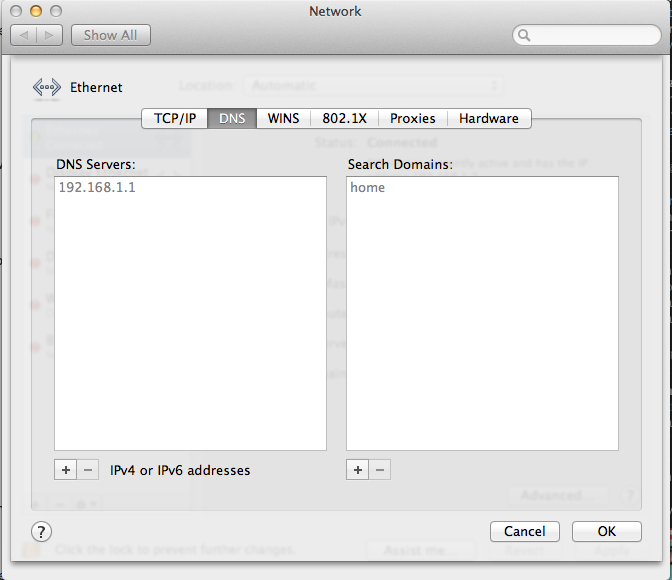
- Click DNS tab
It would look like this:
Take the IP in he DNS Servers box and type it into the input box on this page: https://forms.fbi.gov/check-to-see-if-your-computer-is-using-rogue-DNS.
This will tell you if that DNS IP is part of the DNS servers being shut down.
If you are set to Obtain DNS Server address automatically and you think you could still be at risk you could switch your DNS to use Google’s public DNS until next week sometime. Their DNS server IPs are:
- 8.8.8.8
- 8.8.4.4
If you have found a better way and want to share, let me know. If you have questions let me know. If you just want to say hi, let me know… :)
Hope this helps some of you.

Thanks a lot :)
You’re welcome.