A Primer on DNS and Security
If you’re reading this article you’ve interacted with DNS. In fact, you’d be hard pressed to spend any time online and not interact with DNS.
Many of us spend very little time thinking about it. By design, it’s a “set-it and forget-it” tool that is often set up on our behalf (e.g., our home network, local ISP, office network). Ironically, it’s a critical piece of our security landscape.
This post will explain what DNS is and highlight some of it’s key security considerations.
What is DNS?
DNS stands for Domain Name System (DNS), you might hear it used interchangeably with Domain Name Server (DNS).
It is the mechanism that allows us to find our favorite websites (e.g., amazon.com, perezbox.com, etc…). Technically speaking, it is a redundant, hierarchical, distributed database that is used to pass information about domain names. There are four types of Domain Name Servers that make up the Domain Name System:
[table width =”100%” style =”” responsive =”false”]
[table_head]
[th_column]Server Type[/th_column]
[th_column]Description[/th_column]
[th_column]Layman’s Explanation[/th_column]
[/table_head]
[table_body]
[table_row]
[row_column]Recursive DNS[/row_column]
[row_column]Recursive DNS nameservers are responsible for providing the proper IP address of the intended domain name to the requesting host.[/row_column]
[row_column]This is our gateway to the web, it’s through this server that we access the rest of the internet. They don’t know anything about domains, they are great at asking questions.[/row_column]
[/table_row]
[table_row]
[row_column]Root DNS[/row_column]
[row_column]The authoritative name servers that serve the DNS root zone.[/row_column]
[row_column]These servers are the gateway to the internet. They are the first connection every recursive DNS has to make. [/row_column]
[/table_row]
[table_row]
[row_column]TLD Root DNS[/row_column]
[row_column]The authoritative name servers for the Top Level Domain (TLD) – example: .com, .net, .org. Every TLD has a TLD root DNS.[/row_column]
[row_column]These servers keep a list of all the Fully Qualified Domain Names (FQDN) on their specific TLD.[/row_column]
[/table_row]
[table_row]
[row_column]Authoritative DNS[/row_column]
[row_column]These servers are the authority on domain names. [/row_column]
[row_column]These servers contain all the information associated with a specific domain (e.g., perezbox.com is located 192.124.249.15).[/row_column]
[/table_row]
[/table_body]
[/table]
DNS communicates using the User Datagram Protocol (UDP), over port 53. This won’t mean much to you now, but in future articles it’ll come together and it’s important to understand it is not TCP/IP.
The easiest way to show you the communication flow is to capture it in an illustration:
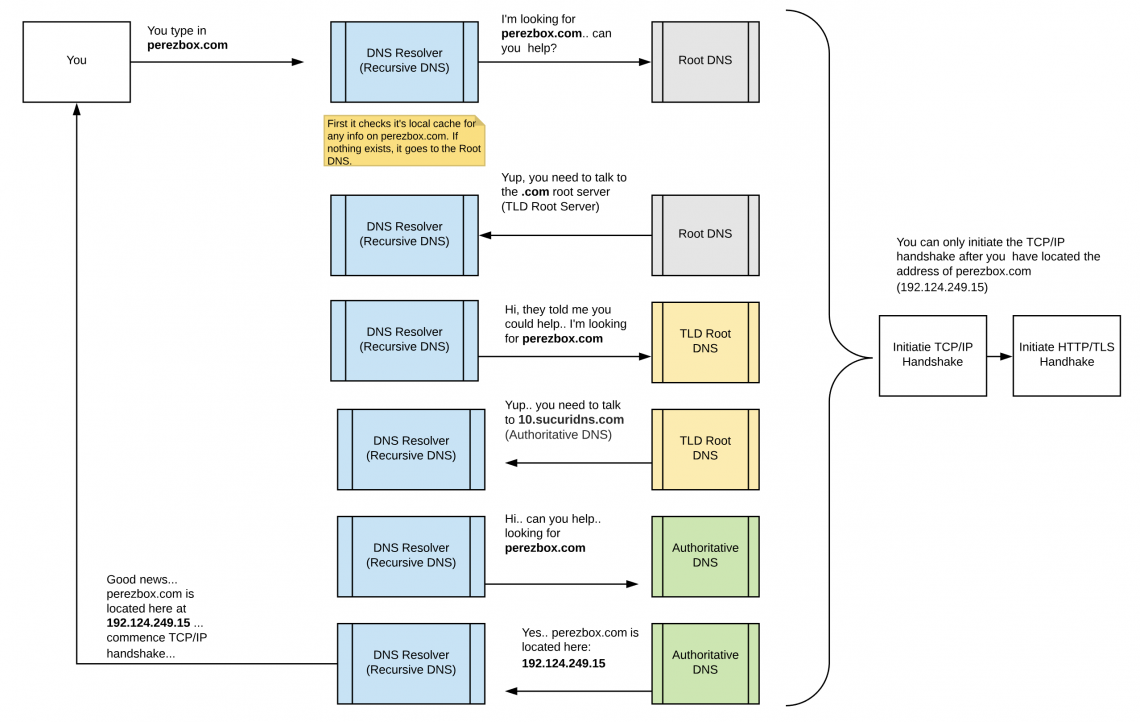
To learn more about the TCP/IP and HTTP/TLS handshakes go to my last article – How HTTPS Works
DNS Security Considerations
Few SMB’s give DNS much thought when thinking through their security. Yet, it’s the one feature that can dramatically affect your business.
An attack on your DNS has the ability to dramatically cripple your organization; it can kill entire web presence (e.g., website) and disrupt your communication medium (e-mail services). What would happen to your business if customers could not access your website? or if you did not receive any emails for a prolonged period of time?
There are aspects of the DNS that are completely out of your control (e.g., Root and TLD Root DNS servers), but they are highly redundant and secure. The issues you can focus on are a lot closer to home, specifically Recursive DNS servers and Authoritative DNS servers.
Five Security Considerations
There are a number of DNS specific security issues to be aware of, but for this post I’m going to focus on the following five:
[table width =”100%” style =”” responsive =”false”]
[table_head]
[th_column]Type[/th_column]
[th_column]Description[/th_column]
[/table_head]
[table_body]
[table_row]
[row_column]DNS Spoofing[/row_column]
[row_column]Also known as DNS Cache poisoning, it’s when an attacker is able to poison the DNS cache in your recursive DNS. The attacker injects bad instructions into the cache, instead of perezbox.com going to 192.124.249.15 it goes to another IP.[/row_column]
[/table_row]
[table_row]
[row_column]Social Engineering[/row_column]
[row_column]This is where the attacker tricks whomever manages the Authoritative DNS zone for your domain into making changes on your behalf. [/row_column]
[/table_row]
[table_row]
[row_column]Availability[/row_column]
[row_column]The key to DNS working is to make sure it’s available. If any part of the DNS architecture is down, you won’t be able to access the internet. This is where Distributed Denial of Service (DDoS) attacks come into play, and why it’s so important you use a good Authoritative DNS server.[/row_column]
[/table_row]
[table_row]
[row_column]Administrative Compromise[/row_column]
[row_column]This is where an attacker is able to steal your credentials and take ownership of your DNS. It’s why it’s so important that you practice good online hygiene with passwords and deploy appropriate controls like 2FA/MFA on your accounts.[/row_column]
[/table_row]
[table_row]
[row_column]Vulnerability Exploit[/row_column]
[row_column]This is out of your control as a user, and speaks to the exploitation of software on DNS servers. I throw this caution out to organizations that might run their own internal DNS and emphasis the importance of functional isolation.[/row_column]
[/table_row]
[/table_body]
[/table]
Planning for DNS Security
As you plan for your security, be sure to account for DNS. Personally, I leverage CleanBrowsing as my DNS Resolver, and Sucuri as the Authoritative DNS for my domains.
There are other technical things we can look to employ to secure DNS, but that’s a subject for another post.
