Rethinking the Value of Premium SSL Certificates
There is an active campaign to reshape how online consumers see SSL certificates, with special interest in shutting down premium certificates by the browsers and security practitioners. This article will shed some light into what is going on, provide some context as to why it’s happening; and it will also offer my own personal opinions and recommendations for the future.
In summary, premium certificates – specifically EV’s – offer more value than we’re letting on because we’re allowing the wrong things cloud the conversation.
Making Sense of the SSL Ecosystem
I recommend reading my primer on SSL, specifically how HTTPS works.
An SSL Certificate is a digital file that binds an identity with a public key and a cryptographic private key. This file is used to verify and authenticate the owner (an identity) of the certificate during a communication exchange between two systems. This SSL Certificate is also what allows you to make use of the HTTPS / TLS protocols on your website.
A site that is leveraging HTTPS/TLS makes use of an SSL certificate to accomplish two goals:
- Authenticates the identity of the website to the site visitor;
- Protects, via Encryption, information as it’s transmitted from the web browser to the web server. It ensures that data in transit cannot be intercepted (e.g., MiTM attack) by a bad actor;
Here is a great example:
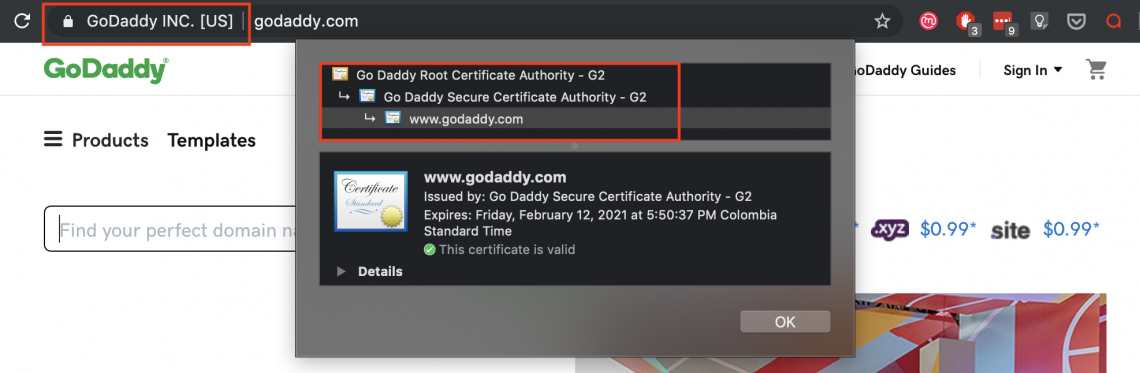
What you see in this example is that this certificate was issued to the godaddy.com domain by the GoDaddy Certificate Authority (CA). These CA’s are responsible for the creation, issuance, revocation, and management of SSL certificates.
How SSL Certificates Are Created
How they go about performing these duties are defined by a voluntary organization known as the Certificate Authority / Browser (CA/B) forum. The output of this forum is something known as the Baseline Requirements (BR), and these BR’s are the rules by which CA’s must abide by if they want their certificates to be recognized by something known as the browsers root store.
Being in the browsers root store is critical for a CA. To appreciate the importance of the browsers root store simply go to September 2017 when Chrome distrusted Symantec’s root certificate. The impact of being distrusted results in every certificate issued by the CA rendering a page like this:
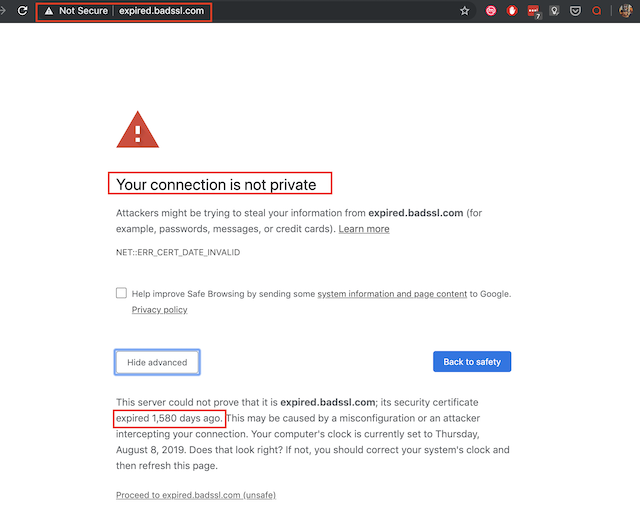
So yes, having a publicly trusted root is the bloodline of every CA. These root certificates are used in the issuance of certificates, and as long as the CA follows the rules defined by the BR’s then root stores will “Trust” the CA’s root certificate in their root store.
Type of SSL Certificates
Under the rules set forth by the BR, CA’s have the ability to issue a number of different certificate types.
For the purposes of this article I’ll focus only on three:
| Domain Validation (DV) | Validating the Applicant’s ownership or control of the domain. |
| Organization Validation (OV) | Validating the Applicant’s identity as a company or individual and the domain. |
| Extended Validation (EV) | Validates the legal entity that controls the website. this is the most stringent validation process available. |
A couple things to clarify:
- All certificates function the same in protecting information in transit, you’re not getting a higher or lower degree of encryption with either certificate, the encryption ciphers are set by the web servers and the minimum values are defined by the BR’s;
- The thing that has always differentiated these certificates to the public has been their treatment on browsers;
- The treatment for DV / OV certificate are the same on browsers, and EV’s have always been that special option;
Treatment of SSL Certificate Types
The thing that has always set the certificate types apart has been their treatment on the browser User Interface (UI). The original premise of the treatment was to enable the web users, like you, to quickly delineate those sites that had gone through additional scrutiny in their validation process.
For these examples I’m going to focus on Chrome because it’s the most widely adopted browser in the market (55% market share as of July 2019). They are also the ones leading the fight against premium certificates and the changes I’ll highlight below.
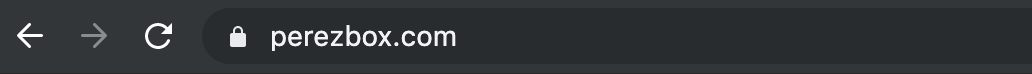
Here is an example of what an DV / OV certificate might look like in the URL inside the Chrome browser today (in 2019):
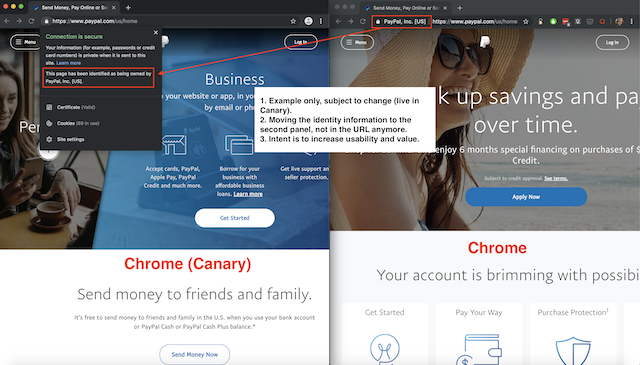
Here is an example of what an EV certificate might look like in the URL inside the Chrome browser today (in 2019):
Here is an example of what the certificates used to look like:
As you look through the examples above you can quickly see what is happening. The treatment of EV certificates is changing dramatically. In earlier versions it was easy to point out those sites that had gone through higher scrutiny in their validation process, and in theory it should have given web users a higher degree of confidence in the legitimacy of the site.
Here is an example of what you can expect in future releases of the Chrome browser:
What you see above is work being done by Google to remove the indicator all together. You can expect the final iteration to potentially look very different than the proposal above.
The genesis of why can be found in Google’s release of a research paper titled The Web’s Identity Crisis: Understanding the Effectiveness of Website Identity Indicators.
The entire paper boils down to this:
In 14 iterations on browsers’ EV and URL formats, no intervention significantly impacted users’ understanding of the security or identity of login pages.
Authors: Christopher Thompson, Martin Shelton, Emily Stark,Maximilian Walker, Emily Schechter, Adrienne Porter Felt – Google
In other words, there was no perceived value of the UI indicators. Because there is no value, Google will proceed with removing them (in the form of burying them deep into secondary panels). You can expect that the next analysis will show that users do not click on the secondary panels, as such their value is further diminished.
Discourse Makes a Solution Difficult
Here are some of my personal observations, points of contention and positions across both sides of the aisle as to why premium certificates are ineffective:
- Even amongst security professional few truly understand the difference between certificate types;
- We never really brought about good awareness to what these indicators were meant to signify;
- The CA/B forum is comprised of a lot of attorneys, this creates a very CYA like approach to development of BR’s – in other words, we avoid anything that might imply liability. This framing makes it difficult, we shy away from things like “assurance” and “trust” and creates an environment of extreme interpretations;
- Massive commercial entities were built around these SSL certificates, such that any perspective from a CA is immediately dismissed because it’s believed to be impartial and beholden purely to commercial interests;
- There are real challenges like collisions in the systems, where two entities could exist with the same name, established under different jurisdictions. Which technically, isn’t really a problem if it’s a legitimate entity;
- We inaccurately try to place value on premium certificates on things like security (e.g., premium certificates curtail phishing). This narrative derails and distracts the conversation;
- Perception of issues exist with the fact that you can have a validated entity that is not the same as the domain (e.g., domains owned by franchises). Which technically isn’t a problem if we refine the meaning of the value of the premium certificate and the assurances it provides;
- As a community there is an “us” vs “them” mentality, where the browsers are good and the CA’s are bad. This has led to a contentious, toxic, relationship between both parties, which does little for the web;
- We lean on security whenever there is no valid answer, never differentiating between practical and theoretical security;
- We claim to be considerate of the greater web, but share very little empathy for the challenges we’re introducing to the consumers (both micro-businesses, large organizations, and passive consumers) of the web;
- The advent of social platforms has given a platform to pundits all around the world, experts and influencers alike, that amplify and convolute the conversation in the interest of goodness, fairness and security while simultaneously adding emotion and unreasonable candor making it impossible to collaborate for a better outcome – then again, this affects almost every industry these days;
- The validation process requires humans, humans are fallible, and it precludes us from automating and making it available to the masses in scalable manner;
- Traditionally, CA’s have been perceived to be stuck in their ways, my own organization included, incapable of keeping up with the evolution of the web – we are probably our own worst enemy;
The Unrecognized Value
Studies have been conducted on both sides of the aisle. On the browsers’ side, a study by Google (The Web’s Identity Crisis: Understanding the Effectiveness of Website Identity Indicators) showed that web users don’t recognize value in UI indicators. On the CA side, you have a study by Georgia Tech (funded by Sectigo) (Understanding the Role of Extended Validation Certificates in Internet Abuse) which tries to show a low propensity for validated domains to be used for malicious purposes. Whether you agree with the methodologies leveraged or the outcomes they offer, I believe the unrecognized value is somewhere in between.
I believe that Google is right, in today’s incarnation of the UI indicators it is absolutely realistic to believe that web users have no understanding of what they mean. I also believe, to an extent, that Georgia Tech’s study (while a bit limiting) speaks to a truth in the low propensity of a validated organization to be used for malicious purposes.
I believe we are missing some really interesting opportunities to help bridge the trust gap online through a structure that is already in place:
- The validations being done for certificates like EV’s, whether we like it or not, and regardless of what the BR’s state, should facilitate a level of assurance of legitimacy to web users.
- While not perfect, the public Web Trust ecosystem built between browsers and CA’s can be the building blocks for something that has a dramatic impact on the great problem of identity assurance and trust on the web.
- There is some validity to the idea that a site that has a premium certificate, specifically EV, has a lower propensity to be used for malicious purposes. It’s not so much the cost, but more the level of effort required to forge all the required documents and forms of proof (which sometimes requires updating gov’t systems).
- Validating an entity is valuable, whether they are doing something malicious or not. The process of validating helps collect real information that can be used later if required.
- Another anecdotal insight comes in what the idea of “validating” actually means to a domain holder. It’s arguable that an organization that is going through the process of validating their domain cares enough about their identity, their security, to have more controls than the average Joe to ensure the integrity of their site. This is especially important when you think how most Phishing attacks happen today (i.e., benign sites being hacked and being used maliciously).
Where I disagree is in the statements that removing the UI indicator is the solution or that EV’s deter phishing attacks.
A failure to understand the indicator doesn’t mean the indicator isn’t valuable, but rather that we should work harder to pull the value forward.
Ironically, there is probably no greater example of the power of awareness and education than Google’s very own #httpseveryhwere campaign. A campaign in which Google drove home the importance of a HTTPS/SSL indicator by leveraging their greatest asset – SERP rankings. This initiative worked to educate consumers to look for the “lock” and the “secure” indicators, which makes me believe we can educate web consumers.
We live in a world where trust online is growing in importance. As such, we should be leaning into solutions that help pull forward that value. There are over a billion websites live on the web, and growing. Web consumers struggle every day with understanding what websites they can / should interact with.
As a community we should revisit the value and purpose of the premium certificates, specifically EV’s, and place emphasis around things like “trust” and “assurance.” We should work to pull that value forward in a way that we can help consumers differentiate and recognize easily.
Disclaimer
In full disclosure, I’m GoDaddy’s General Manager (GM) for the Security product group. This business line includes GoDaddy’s Certificate Authority (CA), which means we sell SSL certificates. The portfolio has considerable depth in the presence domain; features like a Web Application Firewall (WAF), Content Delivery Network (CDN), Security Scanning, Brand Monitoring, Incident Response, Premium DNS, Website Backups and the Sucuri brand.