Security In Open-Source CMS Applications
Open-source CMS applications are no stranger to the battle they face with security. The size of the organizations adopting the platform also has little to do with it – from bloggers to mom and pop shops to Fortune 500 companies; the concern is the same. Can open-source CMS applications be deployed securely within their respective stacks?
There are those that look at open-source and have a general distrust for it. The idea that people can see the code and submit patches makes them uneasy. There are also those who can’t get their head around the general ambiguity of open-source, in which the code belongs to no-one and everyone. What they don’t realize is that most open-source projects have a stringent commit process.
The security perception is still a very real problem for the open-source CMS industry, and many feel it’s unattainble.
The Open-Source CMS Ecosystem
I have come to the realization over the years that the fundamental issue with security resides in the design of the open-source CMS applications.
Of the various CMS’ on the market, there is one platform that has been making the biggest improvements over the past 12 to 24 months when it comes to security – WordPress. They are perhaps the ones most negatively affected by their own design, yet ironically making the most effective improvements. Improvements include the OCD like focus on backwards compatibility and the introduction and use of things like auto-updates. They’ve also started to evolve the design of their application to assume a more security-by-design approach.
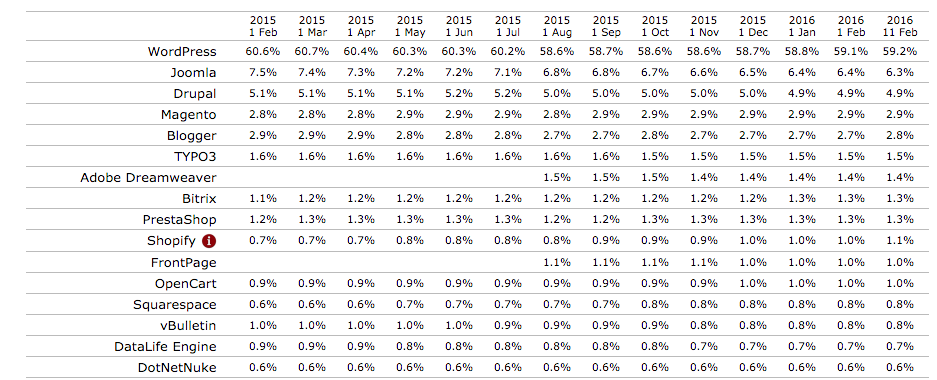
The top 16 CMS applications (source: W3Tech).
It makes sense to me – they have to – with the market share they enjoy and their desire to continue to expand that share, security has to be something quickly addressed. This unfortunately is not something I see cascading to other open-source CMS applications. The biggest issue with other open-source CMS applications is backwards compatibility, or lack thereof. It’s this mindset of, “well if they don’t know what they’re doing and can’t figure out the upgrade they shouldn’t be using our platform.” That’s horrible. The affects have a ripple affect across all CMS environments, and open-source more specifically.
Security Doesn’t Discriminate
Security is the common theme across all technologies. No one platform is immune to the existence of software vulnerabilities. They come in all shapes and forms, and in highly extensible environments, like those today’s platforms provide, it becomes very complicated. Complex things break in complex ways.
Today, the security issues often extend beyond the core of the applications and migrate into the extensible components (i.e., plugins, themes, modules, extensions, themes and templates) that make up the anatomy of today’s CMS based websites. While the core teams invest a great deal of energy and time to maintain and patch their applications, the extensible components of the core are fundamentally different. They belong to third-party integrators and developers, in which their resources are often much more limited.
These security implications are compounded because few people that deploy these technologies truly understand how these applications function and so an apple is an apple is an apple. It doesn’t matter if a security issue stems from the server – or an extension. It’s the platforms fault. This then finds it’s way into the would-be experts who pronounce the insecurities in technologies like open-source or platforms specifically. This vicious cycle continues and spreads like the viruses of old.
Over the past 24 to 48 months open-source CMS applications have been getting hit hard making the front page of most virtual news outlets for what they perceive to be “security” issues with the platforms themselves. The sad truth is that in most instances, whom the proverbial finger is being pointed at is all wrong. There are no absolutes in security, yet that is what we educate and in turn, what our website owners seek.
User Adoption & Security
When it comes to security, WordPress has undoubtedly felt the greatest wrath. It’s of no surprise though, it’s a highly extensible platform built for the end-user first and foremost. It’s what sets it apart from all other CMS applications, and why it enjoys the market share it has. The market share it owns however is a double-edge sword, with user adoption comes an attractive target, own one own them all.
This focus on the end-user is what fostered the user adoption that has fueled the platforms growth globally. However, it’s caught the eye of every would be bad-actor. When the piece of the pie is over 55% of the CMS market (25% of the websites on the web), why wouldn’t you place your emphasis there? That’s the mindset we’re working against.
It’s not to say that the other applications are not targeted, but they are insignificant when compared to the value that the WordPress market share offers. The one exception might be Magento based websites, being it’s an E-Commerce CMS, with it’s motivation being pretty apparent (i.e., immediate economic gain in things like payments, credit card information, etc..). This will inevitably tilt as a motivator towards WordPress as it extends its reach into the E-Commerce space in the coming years.
Regardless, the life line for today’s open-source CMS application is user adoption. Without it, there is no economy for the platform. There is no vested interest to improve it, no one is using it; organization won’t invest time and money, there is no return on investment. This adoption is also directly tied to an applications ability to be extensible.
As technologists, we’ve streamlined the ability for people to create an online presence. What have we done to educate the same people about the responsibilities of having said presence?
Can Security Be Achieved?
Yes, it can. People’s claims that the platforms are insecure or unable to be secured are unfounded and ludicrous, stemming from a lack of understanding of either the technologies or security. As long as there are people, there will be security issues; it’s in our nature to break things.
This blog and our own blog at Sucuri have been on an open-source CMS’ since their inception, as have many of the largest media outlets on the web. A prominent example can be found in closed environments that leverage open-source technologies. Environments like the worlds largest WordPress deployment – WordPress.com. Not to be confused with wordpress.org. The same can be found in a number of other similar implementations, like Joomla!’s own Joomla.com and even much smaller deployments of the same technologies by service providers for their respective customers.
How do they do it?
It all comes down to the basics of how the application is deployed.
Whether a large or small organization, a basic understanding – and respect – for things like Security can go a long way to reducing your overall risk. It’s a mindset. Everything from the server / file level permissions, the configuration of your users and their associated roles, the employment of basic Defense in Depth principles, to your everyday online activities and the integration of services designed to complement your existing administrative functions. A small investment early in the websites deployment phase can go a long way to creating a healthy / secure environment.
If we look closely, the most effective and secure implementations are those in which the role between end-users and website administrators are clearly defined. We have to do a better job of setting expectations and delineating where someone’s responsibility starts / stop when it comes to their own website. If we don’t, the effects will continue to be felt, exaggerated and ultimately continue to have an adverse affect on the open-source technologies we have all love.
Special thanks to my business partner Daniel Cid for always helping me think through my thoughts.
