Website Security is Not an Absolute
I work in the field of Information Security (InfoSec), specifically website security. With that in mind, it’s but one very small piece of a very large pie. Security is complex, even at the 50,000 foot level; within each specific area of the industry, it can get even more complex. It’s no wonder it can feel overwhelming.
I have to remind myself that Security, regardless of which domain you’re focused on, always comes down to three basic elements working in conjunction with one another:
- People
- Process
- Technology
These are not new. In fact, they’re the same three factors we see in the architecture of Information Technology (IT) stacks, and even in the transformational articles on Business. Yet, they are three easiest factors to either dismiss, and rarely are discussed when speaking to security, let alone website security. I’d argue though, that especially when thinking about website security, it should be top of mind and reinforced with every webmaster (i.e., that’s all of you that own a website and are ultimately the final authority on it’s security).
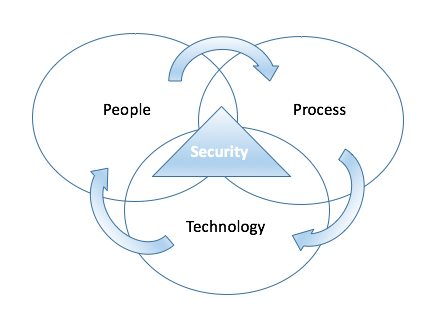
The above illustration attempts to illustrate the symbiotic relationship as I see it, between these three element and security. They are designed to interrelate with one another, yet rarely do.
I. People
The people element is, in my eyes, the most important factor in your entire security posture, you can have ok processes and no technology, and still have a semi-decent security posture for your website if your people understand some facets of technology and security. There is a lot to be said for following the basic principles, like Defense in Depth or Least Privileged.
At the company I work for, we work heavily with websites built on open-source platforms like WordPress, Joomla!, Magento, Drupal and so many other Do-It-Yourself (DIY) technology stacks. These platforms however are built around the ideas of freedom; freedoms to build and share, manipulate and otherwise do what one pleases with their environment. While beautiful ideology, it requires special attention and awareness by the same individuals that employ them to properly manage and administer them.
Freedoms to build and manipulate, does not correlate with the ability to stay safe or secure. Those responsibilities, still fall on the website owner themselves.
The greatest security asset any website owner has, is their own intuition and knowledge of their own environment. With out people; you have technology controls that complicate workflow, inundate with information making it impossible to make sense of the data, or simply add little value. With out people, your processes are empty guides, that offer you little value, with no one to follow them or make them actionable.
II. Process
If you know anything about me, you should know I’m not the biggest fan of processes, specifically stringent ones. I’m not against them when employed with careful thought, but I feel that people often become over-reliant on them and in these situations, they stiffen innovation.
With that disclaimer out of the way, I do believe it to be an important factor that needs to be accounted for in security. Especially when talking to the management of your website. Specifically, because security is rarely your core competency, and so you want to have some guidance in the actions you take when managing your web environment. Something as simple as, “all updates will be applied within 24 hours of a release in my staging environment, and 48 hours in production.”
A good process deployment will be stringent enough to give you good guidelines to follow, but not so stringent you lose the ability to use your own mind.
III. Technology
Technology leads the pack when talking about security for websites, not in importance, but in what website owners today perceive to be the most important and what they invest the most energy into.
It’s the absolute that every website owner looks to employ and yet still find themselves suffering from security issues. While important, it’s perhaps the least important when compared to it’s counter parts.
Technology, has always been designed as a complementary force to your overarching security strategy. The technology itself should never be considered as a set-it and forget-it solution, and yet this is exactly what happens.
In my experience, the over reliance website owners put on technology is often directly attributed to their security issues. Those that depend solely on their technology, are often the first to be affected by a security issue.
Website Security is Not an Absolute
Contrary to popular belief, security is far from an absolute.
I myself find it hard to come up with the right words sometimes, but it’s a continuously moving target / issue that requires constant vigilance to understand and appreciate. I recently wrote on what I perceive to be the greatest challenges facing website security, and it talks to this very point as well.
I spend a great deal with website owners from around the world, and the similarities are always the same and daunting. A technology was purchased, deployed, and yet a security incident occurred. Every toolset was configured, and the environment hardened optimally, and yet an incident still occurred. When we dive in the various facets of the how (i.e., like their People and Process investments) the response is always a resounding – hadn’t given that a second thought, but I purchased this tool. This is especially true in the environments I operate in daily (i.e., open-source platforms), in which the security responsibility of the environment is on the website owner.
What most website owners are failing to realize is that the technology is nothing more than a complementary component, and the real value comes from interrelationship between all three facets, not just one. There is no silver bullet to security, there is your individual risk posture, and the actions you take to address it.

Absolutely nice explanation on WordPress security a complete guide showcasing how to see these security in terms of overhaul experience.