How To Protect Your Business Data
It’s impossible to go a week without seeing some reference to a data breach, whether it’s a write up on what happened years ago, or updates on breaches that are still happening. The two breaches I found most interesting where a treasure trove of business data (not credit card data) was exfiltrated, and subsequently released would have to be the 2014 Sony Hack and more recently the Panama Papers hack. With this in mind, there has never been a better time for more discussion around how we think about data protection in our businesses than now.
I am partial to these hacks because as a business owner, especially one in the website security industry, the threat of a compromise is very real. We work under the guise that someone is always watching and the fact that a compromise is inevitable. As such, a lot of what we do is about minimizing the exposure and impact when it happens. There are many ways to do this as well as many areas to focus on, but one particular domain for us is the protection of the data that keeps our company going.
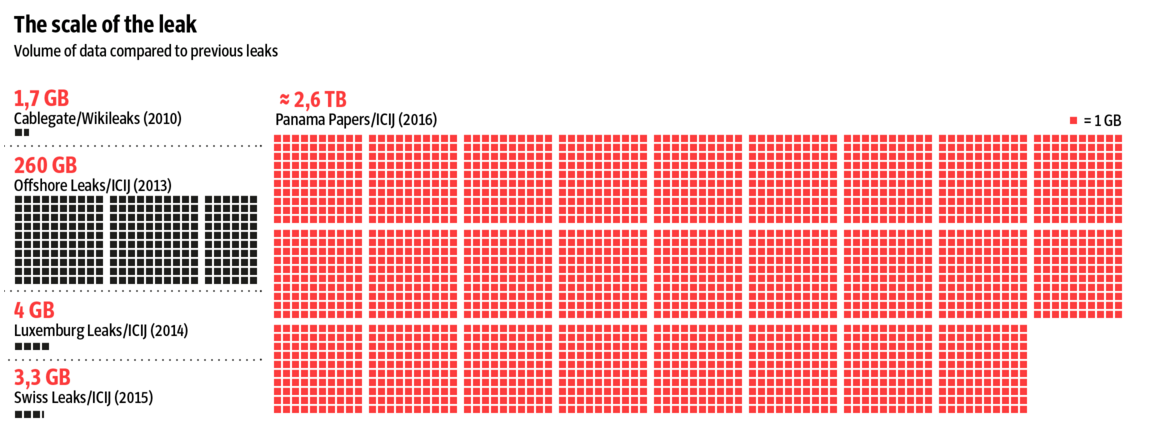
Source: Sueddeutsche Zeitung – Scale of Panama Papers Breach
Unlike larger organizations, small business owners have it easier. While they don’t have roles dedicated to protecting their company data or infrastructure assets, they don’t necessarily always need it. Their greatest advantage is the size and scale of their operation. By placing a little energy early in their formation, they can establish good habits around protection of their business data which can extend years within the business.
Thinking Through Business Data Protection
Data breach reports often shed light and provide an opportunity to learn, fortunately for us there are lots of them. They almost always confirm how similar all businesses are, regardless of size, specifically in the way we collect and manage data. This becomes increasingly more difficult as companies continue to embrace remote work cultures (i.e., geographically-distributed teams), leverage cloud-based storage solutions (i.e., Dropbox, Box, etc..) and struggle with the need of a connected workforce (i.e., mobile devices, etc..). This is especially true with many small businesses, who are often more willing to employ potentially cost-savings tactics to get their businesses off the ground, but that can also have adverse affects long term.
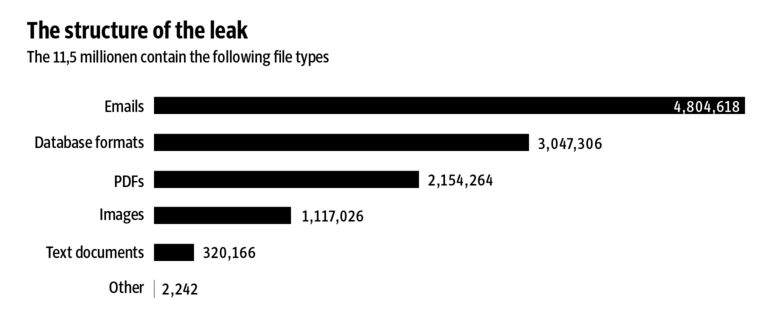
Source: Sueddeutsche Zeitung – Panama Papers – Exfiltrated Data Distribution
As a business you will be charged with collecting, storing and possibly using some form of sensitive data. This data is not always credit card information, but does include information on the business (i.e., HR, payroll, or other similar bits of data). Additionally, your organization might depend on a vendor to provide services that requires access to your own sensitive information (i.e., finances, HR, etc.).
One approach to protecting your data is to think about categorizing it. I categorize it into three distinct states:
- Data in Transit
- Data in Use
- Data at Rest.
Neither are new terms, and have been around for years. Data at Rest is data stored to disk, whether that’s local or remote (think your FY 2014 Financial Close – i.e., All Financial Documents). Data in Use refers to data that is actively being accessed (think a strategic document being worked on). Data in Transit refers to the complete opposite; the data is moving in some form (think communication over a chat medium or data captured on a web form).
Data Classification
One might argue that all data should be protected. Ideal, but highly impractical and impossible to scale. And in many instances, unnecessary.
If everything is important, then nothing is important.
One alternative to assist in the process is to think about classifying the data. In the military, we had things like Unclassified, Secret, Top Secret, and so on. Using similar nomenclature doesn’t hurt, but you can always come up with your own; even as simple as Sensitive and Not Sensitive.
Here is an example of a data classification scheme you can also leverage to help think through your business data classification:
[table width =”100%” style =”table-bordered table-hover” responsive =”true”]
[table_head]
[th_column]Category[/th_column]
[th_column]Description[/th_column]
[th_column]Example[/th_column]
[/table_head]
[table_body]
[table_row]
[row_column]4[/row_column]
[row_column]Highly sensitive corporate and customer data that if disclosed could put the organization at financial or legal risk.[/row_column]
[row_column]Employee social security numbers, customer credit card numbers[/row_column]
[/table_row]
[table_row]
[row_column]3[/row_column]
[row_column]Sensitive internal data that if disclosed could negatively affect operations.[/row_column]
[row_column]Contracts with third-party suppliers, employee reviews[/row_column]
[/table_row]
[table_row]
[row_column]2[/row_column]
[row_column]Internal data that is not meant for public disclosure.[/row_column]
[row_column]Sales contest rules, organizational charts [/row_column]
[/table_row]
[table_row]
[row_column]1[/row_column]
[row_column]Data that may be freely disclosed with the public.[/row_column]
[row_column]Contact information, price lists[/row_column]
[/table_row]
[/table_body]
[/table]
Encryption
It’s important to become familiar with the concept of “encryption”. The act of encrypting is to take something from one readable state and turn it into an unreadable state. The key with encryption however is the ability to decrypt it when needed. Think of it as a vault. It stores valuable assets but it still provides a means to access those assets if needed.
There are two forms of encryption that you should be familiar with, but might be more detail than you need – asymmetric and symmetric encryption. When the same key to encrypt is used to decrypt, this is known as symmetric encryption. When one key is used to encrypt and another to decrypt, that is known as asymmetric encryption.
Data in Transit
When working with data in transit, data objects are moving from point A to point B. When it’s moving between two points the data is, and should be, encrypted. Today, in many instances, it’s achieved using the Transport Layer Security (TLS) protocol and in many instances the tools we use already facilitate this form of encryption.
Examples include:
- Emails (i.e., Google Apps)
- Chats (i.e., Slack)
- Social (i.e., Facebook, Twitter)
- Cloud storage communication (i.e., Dropbox, Box)
Many of these mediums employ the secure communication required when accessing and using their services, so there is little for business owners to worry about in that regard. They don’t account for all things though, and those things might include securely accessing your network. To achieve something like this when on public Wifi you might want to consider using some form of commercial VPN provider that helps encrypt the communication between your location and your company’s network.
This also doesn’t talk to encrypting data flow for things like your website (which is another conversation) but something worth thinking through as well.
Data in Use
By design, data in use requires the data to be accessible while it’s being worked on. To work on it, it must be in its unencrypted state. As such, the act of securing it can be complicated. For data that’s in use, the best strategy is employing strong access controls.
In InfoSec, there is a principle known as “Least Privileged.” It talks to the idea that you give people only the access they require to do their job, for as long as it is required, but not more. I’d say the same can be applied to data in use. Give whomever requires access, access, but for only as long as they require it. Once the use is complete, ensure it moves from Data in Use to Data at Rest.
Note that many of the data storage providers will give you enhanced controls that might include removing someone’s ability to delete a file from the network, or modify an existing file. Tightening these type of controls can be very valuable, especially when thinking about potential insider threats, or bad actors set on total destruction once in your network.
Data at Rest
Data at rest is where we all fall flat on our faces, not just as small businesses; it’s also where the biggest weakness can be seen in both the Sony and Panama Papers hacks. We as humans do a really bad job of maintaining data within our environments. I say this as my own realization as well. It’s almost impossible to fathom the amount of data you accumulate in your business in a week, a month, or over a period of years.
I used to be a big proponent for TrueCrypt, that unfortunately met its demise a few years back when the project was abandoned. I have yet to find a suitable replacement, but each OS has its own built-in technologies. Microsoft for instance integrated BitLocker in its Vista OS and higher, and Apple has FileVault. Each are good solutions for local environments, but can prove challenging when working across a network or team.
What I have found to be most effective has been the use of GNU Privacy Guard (GPG), on a MAC using GPGTools. Once installed, a user can elect to encrypt / decrypt between files or folders. As a user you’re able to maintain a repository of public keys for all recipients in the local key manager as well. Even though we might use a number of available storage providers, these cloud technologies don’t do away with the need to secure your data. In many instances, they secure their networks and communication to their networks. However, if a bad actor has access to your machine or another machine that provides access to the network, all data is accessible.
We also can’t forget about emails. Emails float between the Data in Transit and Data at Rest fluidly. This makes it exceptionally difficult, and also extremely important. More attention is placed on this communication medium. The best solution I have been able to employ that scales as the team grows, is the use of the OpenPGP standard through Mailvelope using the same GPG keys created for local data. What this does is not only ensures that information is encrypted in transit, but ensure that while it’s at rest in the inbox it too is encrypted. As we can see in the diagrams above, email is often something that we all forget, but probably the easiest to account for and in many instances can be the most damaging bits of data.
Protecting our Business Data is Critical
As my company continues to grow protecting our business data continues to be top of mind. I would encourage all other business owners to consider it as well. We have a responsibility to our customers and employees to keep their information safe and away from curious eyes. To do this, above, I’ve provided a few ways to think about data protection. I offered some thoughts on classification, a brief introduction to the idea of encryption, and an explanation on the three states of data:
- Data in Transit
- Data in Use
- Data at Rest
With this information, you should be armed to start thinking about your own data protection needs. As small businesses, we don’t have the luxury that large companies do when it comes to resources (both in terms of people or money) so it falls on us to stay diligent in the way we conduct business, and security must stay at the top of mind.
The biggest challenge I expect any company to have is adoption once implemented. It’s easy to write processes and demand adherence, but if it doesn’t come from the top down it will fail.

Re truecrypt I wonder why you do not mention one of it’s successors like veracrypt?
Hey @H_Trickler:disqus
Because I’m not familiar with it.. :)
I should definitely take a look though… you like it?
Tony
I had compiled Truecrypt 7.1for Linux a from sources and since that is the version which had kind of a security review that is what I still use.